Archive for the ‘Ask the Expert’ Category
Alan’s Cloud Tip of the Month – March 2013 no comments
 Why move to the cloud? Here is March’s quick cloud tip:
Why move to the cloud? Here is March’s quick cloud tip:
Cloud technology optimizes existing resources…
Suppose your company is facing hard times in managing hardware and software. Let’s say your servers are running extremely low on space, and there is not enough room left for any new data to be stored. To overcome such a situation, cloud services can be employed. In turn, existing servers get a rest from the over-loaded traffic, and the work environment of the company becomes more synchronized.
Moving to the cloud optimizes your resources, but with the help of managed cloud services, businesses are able to focus time and attention on other business-related activities.
Follow Us :Share :
reCAPTCHA: digitizing the printed word, one spam filter at a time 7 comments
 In 2009, Google went from having around 20,000 employees, to having millions of people all over the world working for them. Well… sort of.
In 2009, Google went from having around 20,000 employees, to having millions of people all over the world working for them. Well… sort of.
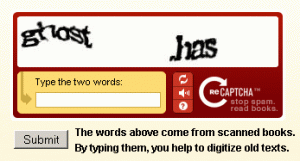
You might already be familiar with what is pictured below. If not, let me explain to you a little bit about something that I was recently informed about –this magical thing called “reCAPTCHA”.
 In the year 2000, I was worried about passing the 4th grade. I was anticipating that all the computers in the world were going to explode due to Y2K. I was hoping that I could fend for my family and not die of Dysentery on The Oregon Trail. Needless to say, life was rough.
In the year 2000, I was worried about passing the 4th grade. I was anticipating that all the computers in the world were going to explode due to Y2K. I was hoping that I could fend for my family and not die of Dysentery on The Oregon Trail. Needless to say, life was rough.
But Yahoo!—and hundreds of other web companies, for that matter—were dealing with a much larger epidemic than Dysentery—spam. No, not that gross, canned mystery meat, and definitely not George Michael’s Wham! This kind of spam is something (debatably) worse than both… combined!
We’ve all encountered spam in our email inboxes, but now, thanks to Luis von Ahn, we also have all run into what is stopping most of it.
Luis von Ahn grew up in Guatemala and worked in his family’s candy shop as a kid. Later on in his life, along with his college advisor, he was hired by Yahoo! to create a program that could tell the difference between a human and a form bot. They came up with “CAPTCHA”, which—and I’m serious here—stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.”
While the name isn’t exactly the work of genius, these brilliant guys created a challenge-response test that could be predominantly passed by humans to block those evil form bots and eliminate as much spam as possible. These computer-generated, squiggly words are made so humans can read and submit them, but that computers cannot.
After becoming extraordinarily successful off this creation, Mr. von Ahn still found a weakness in his own program. The flaw? The 10 annoying seconds wasted while someone types in a CAPTCHA every time they come across one. After turning down a personal offer from Bill Gates to work for Microsoft and winning the MacArthur Fellowship Award in 2006, von Ahn re-created CAPTCHA and titled it…erm… reCAPTCHA! Luis von Ahn believed this new idea would be good for humanity, and as far as some other types of crowdsourcing go, I agree.
In 2009, Google bought reCAPTCHA and released it upon the masses. Now, what reCAPTCHA does is take the words we type in and use them to digitize old books and newspapers. These books and newspapers are scanned and turned into text-images by using “Optical Character Recognition” (OCR). The problem remains that computers still cannot read text as well as humans. A simple word like “of” could be interpreted as “at,” since old books and newspapers may have words that are damaged or hard to scan.
Here is where the superpower of humans comes in! We can read the word “of” and correctly submit “of,” instead of “at”, along with a computer-generated CAPTCHA word. So a reCAPTCHA image is combined with a CAPTCHA word, and placed at the login of something like an email. If we get the CAPTCHA word correct, we are in-there-like-swimwear. Even if we get the reCAPTCHA wrong and cannot decipher it ourselves, but get the CAPTCHA, we are still allowed access. The reCAPTCHA word will be tested by many other humans to increase the likelihood of it being deciphered correctly.
Using the aforementioned example of the word “of” being read as “at”, if people keep typing “of”, the word “of” will digitally replace the word that the OCR program recommended. After some time, millions of people are deciphering these scanned reCAPTCHA words and creating digitized versions of old New York Times newspapers and classic books for Google!
In months, with the power of reCAPTCHA and humans’ ability to read damaged words, 20 years’ worth of material is digitized and transcribed thanks to… well… you…me… Alan Rosenberg… maybe Luis von Ahn and Bill Gates… your mom? Everyone! In time, thanks to Luis von Ahn and his team, we will all be a part of digitizing millions of old texts to be distributed online. Now, where are our paychecks, Google?
Follow Us :Share :
Alan’s Cloud Tip of the Month – February 2013 1 comment
 Why move to the cloud? Here is February’s quick cloud tip:
Why move to the cloud? Here is February’s quick cloud tip:
24/7 availability, and performance-oriented infrastructure…
When we talk about cloud technology, there are concerns. One main concern is whether or not the technology can cater to clients’ needs, and another is the scalability of the environment created. If such questions boggle your mind, don’t worry. Managed cloud services will do both for you. Cloud monitoring and cloud migration of data from one server to the cloud server are two features (among many others) that are catered to by managed cloud service providers.
Follow Us :Share :
Alan’s Cloud Tip of the Month – January 2013 1 comment
 Why move to the cloud? Here is January’s quick cloud tip:
Why move to the cloud? Here is January’s quick cloud tip:
The cloud follows the “pay-for-what-you-use” model…
This particular characteristic of the cloud focuses on the fact that cloud computing and managed cloud services are truly cost-effective. This means that users will have to pay only for the amount of service used by them. This way, money spent on improving business through the cloud does not entail extra, unnecessary expenses. Small to medium businesses benefit the most from the type of facility the cloud offers, but large businesses benefit as well.
Share :
What makes an IT Professional? Better yet, a TurnKey Professional? 1 comment
How are you feeling this week? I’m only asking because I’m not sure how to begin this topic. Let’s see, not too long ago, one of my co-workers mentioned that some of our competitors were writing blog entries on what it’s like to be an “IT Professional”. This has actually been something that I’m curious about myself.
What makes an IT Professional? I mean, IT (Information Technology) is such a large umbrella. So I did what I always do when I need to know something: Google. You would be surprised—well, you might not be—about the number of articles out there that deal with this very topic. Hundreds of “IT Professionals” all list their own explanations of what an IT Professional does.
Rather than bore you with yet another article on what an IT Professional does in general, I would prefer to take you into the world of a “TurnKey Professional”. These are probably one in the same, as a common denominator through all of the articles on IT professionals was this idea of wearing multiple hats; metaphorical hats, in this case. This could be anything from fixing a certain type of software, to providing customer service to a local client. If you’re really lucky, you may even get to work with a businessman or salesman.
In no place did I see this idea chiseled deeper into stone then at TurnKey Internet. On some days, I’m just your friendly, neighborhood slayer of tickets. This extends from any support issue as small as resetting a password on a locked out cPanel account, to deploying a major upgrade to new technology. On other days, I might be working on LiveChat, attempting to sell one of our many services—everything from dedicated servers, to colocation, to domain registration.
A TurnKey Professional is a jack of all trades, if you will. We each have skills that we must call on in a moment’s notice, to best service the needs of our customers. Isn’t that what an IT Professional is supposed to do? I’m not 100% on that, but I know here at TurnKey Internet, that’s what we do.
Having team members who each possess different skills, leads to a diverse, all-encompassing set of solutions to common issues that any IT Professional may run into. You know, that’s why I love working here. There are always multiple ways to solve an issue, and here at TurnKey, we usually end up employing many of them—if not all of them—to solve our clients’ needs. It’s quite refreshing.
Well, that’s just another little bit of information I wanted to share with you. It’s another way to show you Turnkey-lovers that I love what I do; another piece of information to share and bond over.
Until next time…
Follow Us :Share :
How to: Build a Hosting Business 1 comment
A couple of weeks ago, my co-worker, Joe Schoonbeck, came up with a brilliant idea for a post. He suggested we write up a quick “How-To” on some of the essentials you need to begin a hosting business. What a simple, yet profound idea. If I had a dime every time we received questions about how to set up hosting, I would be able to buy a triple with cheese and a large fry from Wendy’s. Enough of this talk about food; let’s get down to business.
Now, this list of ideas is by no means set in stone. These are just a few steps that I believe will give you a good foundation to build your business upon.
Step 1 – Decide and Buy
This may seem like a no-brainer, but it is important to determine which type of reseller account suits your needs. Unlike spandex, one size does not fit all. You see, at TurnKey Internet, we sell different types of reseller accounts: alpha, master, and WHM (web host manager).
Each reseller account has its pros and cons, but we’ll leave that for another article. For this entry into the TurnKey diary, let’s just keep it very high-level. Alpha accounts can resell Master accounts and WHM accounts, while Master accounts can only resell WHM accounts. Then, the poor, old WHM accounts can only resell cPanel accounts. This allows you to resell multiple accounts on your website.
Once you decide which account is best for you, purchase it.
Step 2 – Create
I had an intense, internal debate about step 2. Initially, I was thinking about skipping right to Step 3 (configuring your DNS), but it didn’t make sense to me to get into that if you have no site to share with the world.
You can take multiple steps in setting up your website, so I will be brief. You can use TurnKey’s website builder that is included in our reseller packages. Or, maybe you have a developer who creates fantastic websites in his/her sleep. The choices are limitless on this step.
Step 3 – Setup (Part I: Your DNS)
For the sake of this article, I’m going to assume you do not know what DNS is. I’m going to instead share how I teach what DNS (domain name system) is to our newbie engineers. You see, I compare DNS to a post office system. You have your streets and your addresses, which allow people to find your place of residence. That’s what DNS is, in a nut shell.
You have your website, and in order for others to see your masterpiece, you must first tell them where it is. You do this with your DNS. You have your DNS record, which contains your website’s IP address and your nameservers. Your IP address is essentially like the number on your mailbox. Your nameserver(s) would be the street(s) on which your house resides. You have to setup your DNS in order for others to visit your site.
Step 4 – Configure
Now that you have your site online and users purchasing hosting from you, they will inevitably need support. This could be with anything, from support for setting up your clients’ websites, to adding space to their account.
You will need some point of communication that you can use to speak with your clients. Our TurnKey reseller accounts each come with free helpdesk software included, which you can white label in your company’s name. This allows you to have a way for your customers to easily and efficiently submit tickets.
Step 5 – Setup (Part II: Extras)
When I say “setup extras”, these are items that can add increased functionality to your hosting company. While this step can be rather large, we will just stick to a few of the basics.
If you’re selling anything on your site, you will need to install an SSL certificate. This basically encrypts your users’ connections when they submit orders to your company. I would say this is just as important as your website. If you don’t happen to have an SSL certificate lying around, you can request a FREE SSL with your TurnKey reseller account. If you’re going to be accepting orders, you may need a billing system that can help keep those orders in line. Enter—one of our most popular free extras—a free WHMCS license.
Now, there are no exact steps, but these can give you a good foundation for beginning your hosting account career.
Until next time, Turnkey Lovers!
Follow Us :Share :
Is Facebook Really Free? 2 comments
Is Facebook really Free?
As many of you have probably noticed, certain aspects of Facebook are beginning to cost money. How do you feel about it?
Since we all started using Facebook we have enjoyed the free social media interaction, the no cost way of communicating. We have had a brand new way of keeping in touch with old classmates, high school sweethearts, co-workers etc. Being able to reach out to all ends of the world in a split second, and see how everyone that you care about is doing, without having to actually speak to them. It has had its perks.
Over the last year or two businesses have been able to start using Facebook as a way to reach out to more people. What better a way to gain awareness than word of mouth, and there’s no better online word of mouth source than Facebook. Still, always free.
Now Facebook is ingrained in our everyday lives, whether we like it or not. Companies are offering coupons if you “like” their pages, businesses share their products right on their profiles, you watch commercials with “like our Facebook page” at the end. Hundreds of thousands of people are just a “click” away from being able to see your adds, promotions and whatever else you have chosen to show.
Everything was great, free advertising…..
Not for long. Facebook saw that money could be made – or rather convinced the Stock Market they could make money. The amount of people and businesses that promote themselves, could in some way benefit the pockets of Facebook. So of course, it changes. Now instead of being able to reach out to all of your followers, facebook highlights and directs you to to premium ways to pay to reach a certain percent of them beyond your standard reach. The more you pay, the more people you can reach. You can pay for an add campaign that targets a certain group of people, and again, the more you pay, the more people you can reach. Facebooks way of getting their piece of the pie – after all they are the #1 social media platform in terms of volume and eye balls. The real question, how do businesses (those being the people who will pay to use Facebook) fit in, and how does Facebook find a way to make money without loosing its popularity?
Do we have a choice? Of course we do, we can stop using Facebook. Yea, right, we all know that’s not going to happen. So businesses will spend the few dollars and reach as many people as possible, facebook will re-invent ways to make money – and the cool factor of years ago of Facebook will be replaced by the highest bidder on who’s cool message is going to be promoted more.
Be sure to visit our Turnkey Internet Facebook page for your chance to win “The New Ipad” – and read about our summer long social media event!
Follow Us :
Share :
Is the Internet about to Stop? What happens when there are no more IPs? no comments
Howdie do Turnkey Lovers,
Jeremy here again. This past week, one of my co-workers made an interesting comment to me. He said, and I quote, “One day when the internet runs out and we have no more IP’s, what will people do then?”. Now this lead me to an interesting set of questions. Is my co-worker right? Are we going to run out of the “internet”, will it just ‘stop’ workign since IP’s are becoming scarce and how will that affect hosting (SEO/cPanel/Reseller).
Well, in order to answer these questions, we must first look at what an IP even is and are their different types? Now, for most of you technies or self-proclaimed geeks, you are probably shaking your heads saying, that’s such a dumb question. Of course there are different type of IP’s and everyone knows what IP’s are. For this article though, let’s assume that you were from a distant planet who knew nothing about the internet. You and you’re family had decided to make your way down to this glorious planet for a vacation.
Upon arriving, you notice everyone is talking about social media, smart phones, computers, and tablets. You’re quite the inquisitive alien life-form and begin to wonder, “What do all of these things have in common?”. Enter Google. You begin to search the internet as one of your new Earth friends, let’s call him Jeremy(no relation), informs you that you need to find a computer and Google Internet. Upon your search, you discover that the internet is essentially a cluster of computers connected together globally using something called a TCP/IP Protocol.
This protocol, as they call, it seems to be rather important. So important that I included the definition from Wikipedia below on it:
The Internet protocol suite is the set of <http://en.wikipedia.org/wiki/Communications_protocol> communications protocols used for the <http://en.wikipedia.org/wiki/Internet> Internet and similar networks, and generally the most popular <http://en.wikipedia.org/wiki/Protocol_stack> protocol stack for <http://en.wikipedia.org/wiki/Wide_area_network> wide area networks. It is commonly known as TCP/IP, because of its most important protocols: <http://en.wikipedia.org/wiki/Transmission_Control_Protocol> Transmission Control Protocol (TCP) and <http://en.wikipedia.org/wiki/Internet_Protocol> Internet Protocol (IP), which were the first networking protocols defined in this standard.
Not to be the alien to leave information out, you decide to research further into the Internet Protocol (IP). Definition is below:
The Internet Protocol (IP) is the principal <http://en.wikipedia.org/wiki/Communications_protocol> communications protocol used for relaying <http://en.wikipedia.org/wiki/Datagram> datagrams (also known as <http://en.wikipedia.org/wiki/Network_packet> network packets) across an <http://en.wikipedia.org/wiki/Internetwork> internetwork using the <http://en.wikipedia.org/wiki/Internet_Protocol_Suite> Internet Protocol Suite. Responsible for <http://en.wikipedia.org/wiki/Routing> routing packets across network boundaries, it is the primary protocol that establishes the <http://en.wikipedia.org/wiki/Internet> Internet.
Or in lamen terms, it’s an individual address that every computer, smart-phone or tablet uses to connect to the Internet. Ok, I think the alien role-playing has gone on long enough. Let’s bring this back to Earth. Now let’s say you read my previous article and learned a bit about cPanel/Reseller hosting. It’s probably safe to assume that you’re aware that when you purchase a reseller or cPanel account from Turnkey Internet at http://www.turnkeyinternet.net/ , you can receive a dedicated IP. Essentially, the address to which you can host your website.
That IP is from the IPv4 family or the Internet Protocol Version 4 family. Now if we reference the statement made by my co-worker made earlier in the article, you can safely assume there is a finite number of these type of IPs. 2^32IP address or around 4.29 Billion IP addresses. The 32 is essentially 32 bits or 192.xxx.xxx.xxx. That’s a rather large number, but so is the number of people joining the internet every day. Eventually, those IP’s will run out which will force a new IP family, IPv6. Now, I won’t bore you with the details about the differences between the two families, but there is one key difference, the number of IPs each family can produce. For IPv6, they can make 2^128 available address or 340,282,366,920,938,000,000,000,000,000,000,000,000. The 128 is essentially 128 bits or 192.xxx.xxx.xxx.xxx.xxx(I think you get the point).
So to answer my co-workers question, which I’m sure you already know the answer to about running out of IPs, we just switch to a new IP family and the Internet will live on. Now, for the win, how does this affect your Turnkey Internet cPanel/reseller packages?
Well to be honest, the effect will be pretty negible on the cPanel/reseller side of things. The biggest noticeable difference will come during the transition period of switching to IPv6 as DNS propagation will take a bit of time to respond to the new IP addresses. This could affect your sites load times during the transition period. Other than that, the main difference will be cost. IPv4 will and already is becoming a premium as these IP’s are being filled by potential new Turnkey Resellers as yourself. Only a few companies are offering the IPv4 IP’s at a low, competitive price such as Turnkey Internet. Which means, you need to get them while you can. Those who for instance start a web site a year from now when there are no more IPv4 addresses left, will only have a new IPv6 address, making their web pages possibly slower to load because of how the Internet as a whole will be using dns and specialized proxy systems to ‘store/forward’ to connect IPv4 and IPv6 together (think of it as a 4 lane highway that connects 2 big cities together). IPv4 and IPv6 connections between each other will be congested on that 4 lane highway at times – which is why it’s very important to try to get yourself hooked up with a good web site that includes IPv4 space (and a provider that supports IPv6 too!). TurnKey of course has that already setup for you and has been a leader in this space offering both for some time.
Well that was quite a handful or is it mouth full? I’m not sure anymore. The reality is – the Internet will continue, IPv4 address will run out (or already are out, depending on which provider you are with) – and IPv6 will be a transition behind the scenes that may be a little bumpy and congested for people, but will happen.
Until next time Turnkey Lovers – Jeremy
Follow Us :
Share :
5 Tips to Double your Twitter Followers in 14 days! no comments
At TurnKey this summer, we’ve amped up our social media attention across the board through our new social media contest to help you learn to leverage social media to grow your online business presence. We are giving away some great prizes, like an iPad 3, visa gift cards, and lots more daily contests too! So be sure to check it out.
TurnKey in the past has focused a great deal in online marketing, online discussion forums, reputation building – and of course SEO based content. But one area we had not focused our efforts as heavily into was the core social media arena of Facebook and Twitter until recently.
As we have focused a great deal of time to leading up to, and planning our summer social media campaign – we setup new social media tabs on our web pages, designed a central landing web page, mapped out a schedule of content to write and release, and organized a concept around a contests to help make things a bit more fun for everyone. We have seen some great success with certain strategies we’ve used in the last month, especially with twitter.
Here are some great tips on how to grow your Twitter followers:
#1: Communication is a 2 way street! Tie your followers in with back and forth communications. If you offer a product or service, this is a great place to accept support requests, so others can follow the conversation and learn more about your company. Perhaps people will find you because of the key words used in the conversation, or your potential clients who are checking you out before making a purchase will just see how great you are at customer service!
#2: Follow the leader! It sounds funny, but the reality is twitter like most social network web sites operate on the concept of social circles. If someone is interested in cupcakes, they may be among the 88,573 followers of Sprinkles on twitter – and chances are they are interested in something to do with cupcakes. When you follow Sprinkles, with your business – then the 88,573 followers are going to have your business factored into their social circle in one way or another. If your business happens to also sell cupcakes, or other tasty treats – then its very likely next time those 88,573 followers login to twitter they may be recommended to follow your twitter account!
#3: Become a Leader by Following the Followers: this sounds counter productive, but the reality is if you follow someone, then you show up on their dash board and are highghly considered for the social circle recomendations. Lets use our Sprinkles cupcakes twitter account example above. They have 88,573 followers – if you take the time to look through their followers, and follow 500 of them, on average you are going to see a chunk of them follow you back. within a week. Stick to active twitter follower accounts, and you can rotate out the one’s who don’t follow you back, with new ones. Twitter limits you to 1,000 people you can follow until you grow your own following past the 2,000 mark. Using this tactic is a great way to gain followers who are intersted in a specific subject! This is one of the big secret tips used by those expensive SEO and Social Media Firms – but its so basic you can do it yourself for free.
#4 Remember the 3 C’s – Content, Content, Content: Sure its a dime a dozen out there, not even a dime these days in the online world economy to attract followers. The secret is to offer content that potential followers will find intersting that relates to something you might be promoting or doing – then be sure to tweat and re-tweat about these subjects. If you make cupcakes, and there is an online article about new gluten free cupcakes, tweat about it and link to it. Your followers and social circles will locate you in regards to that content. If you happen to be dealing in a subject matter that has high media awareness tweet about! If you are the marketing/PR person for a law firm, and a big national legal court case is hot in the news – tweet about the case daily linking to intersting comments, or better yet write your own on your blog and link back via a tweet!. You can find large numbers of followers in a very short period of time if you can tie in with big events when you offer something intersting to say.
#5: Re-tweeting 101 : Re-tweeting is the action of looking at other twitter feeds/accounts and re-posting their tweet on your twitter account. It’s as simple as clicking the re-tweet button (hover your mouse pointer over the twitter post you want to retweet, and the link to re-tweet appears). Re-tweet content that matches up with what you tweet and discuss, and you now further interconect your social circle with their followers, again leading more potential followers to now have relevant recomendations to consider following you!
So how do you double your twitter followers? Hard work – yes, but Smart work is the key! These tips above are a great way to get people to pay attention and follow your twitter feed. With some time each day, you can double your following in 14 days or less!
Follow Us :
Share :
Securing your cPanel Dedicated, Cloud or Virtual Server 2 comments
 One of the most frustrating things that can happen to shared hosting provider is to find that one or more of their servers have been compromised. As a shared hosting provider we are responsible for maintaining the integrity of our servers and the client data residing on the server. Not always an easy task.
One of the most frustrating things that can happen to shared hosting provider is to find that one or more of their servers have been compromised. As a shared hosting provider we are responsible for maintaining the integrity of our servers and the client data residing on the server. Not always an easy task.
What makes securing a shared server such a challenge? Well, the intrinsic problems that come with having dozens, if not hundreds, of individual users accessing a single server should be obvious. Each client has the ability to upload any scripts they desire which are rift with security holes due to poor design, coding errors, or just plain laziness on the part of the programmer. (A good example is the continued use of “register_globals” by many PHP scripts…a sure guarantee of an injection attack.) On top of that, a majority of shared hosting clients are not that entirely (if at all) well versed in how to maintain their sites and fail to keep their scripts updated.
But don’t be discouraged as there are some simple steps you can take to help make your servers more secure against many of the more common hacks. I’ll be outlining the security steps I take when setting up new servers. Note that I have a few tricks that I won’t be sharing since I don’t want to give the script-kiddies too much info. Also, I’m only going to give you a brief overview of the steps. In future articles I’ll get into the details of each step and how to implement them.
- Disable dangerous PHP functions. These include exec(), passthru(), shell_exec(), system(), proc_open(), popen(), and show_source(). Some clients might complain that some of their scripts no longer work, but the security this one step provides far outweighs a few broken scripts.
- Secure your /tmp folder. The latest versions of cPanel do this by default now, but it’s always good to go back and check. And while you’re at it, make sure your /usr/tmpDSK file is large enough. It defaults to 512K, but personally, I’d resize it to 1GB or better.
- Recompile Apache and PHP to add additional security features. cPanel makes recompiling and enabling most Apache and PHP features very simple via the EasyApache configuration tool. At minimum, security wise, enable Mod_suPHP and Mod_Security.
- Disable php.ini overrides in suPHP. suPHP forces all users scripts to run as their username. This prevents users from running any scripts as root or nobody. It also disables the ability to override php.ini settings in the .htaccess file. Unfortunately, by default, users can still create custom php.ini files that will override the system-wide version. Thus, if left in this state, they can reactivate the disabled functions from above. You can easily fix this by editing the /opt/suphp/etc/suphp.conf file and uncommenting the three lines in the [phprc_paths] section.
- Configure mod_security. Now that you have mod_security compiled in, you need to configure it. I suggest using the GotRoot rules (http://www.gotroot.com/mod_security+rules) and ConfigServer ModSecurity Control (http://www.configserver.com/cp/cmc.html). Be prepared to spend some time tweaking the rules, but in the end, well worth the effort.
- Install ConfigServer Firewall. CSF w/LFD (http://www.configserver.com/cp/csf.html) is probably the best free firewall protection I’ve used. Easy to install and manage and it works right out of the box.
- Install Rack911.com’s Symlink Patch. By default, Apache allows you to symlink to ANY file on the server. This means a malicious user or hacker can symlink to system configuration file and other users commonly known scripts config files and read them. While you could simply disable symlink altogether, that would almost certainly break many system functions. Rack991 generously released a patch that simply prevents the system from creating a symlink to files that are not owned by the user.
- Secure SSH. You can change the SSH port, but I’ve found that it’s not really all that beneficial as port scanners can eventually find the port and it just makes our job harder as admins. Instead, simply don’t allow SSH for ANY cPanel user, not even jailed. And add “PermitRootLogin without-password” to your sshd_config file. This will only allow you to SSH into the server is if you have a valid SSH key in the authorized_keys file (Be sure to add that BEFORE you change the sshd_config file).
- Install Maldetect. Install Linux Malware Detect from R-fx Networks (http://www.rfxn.com/projects/linux-malware-detect/). While not perfect, it does give that extra layer of detection.
- Review your Tweak Settings. Under Mail, set your Emails per hour limits to a low number (100); enable prevent NOBODY from sending mail; enable Add X-PopBeforeSMTP. These settings will put a strangle hold to mass-mail spamming and if you do have a spammer, quickly find who it is.
While implementing these steps will not 100% guarantee that your server will never be compromised, it does put you on good footing to prevent a vast majority of the types of attacks that you might see. I’ll touch more on each of these points in later articles and on other things that can be done to give you that balance of security vs. usability that shared hosting clients require.
Follow Us :Share :