Top 8 Features of VPS Cloud Servers to Maximize Performance & Scalability of your Business no comments

As businesses continue to rely on technology for daily operations, the need for reliable and efficient servers has never been greater. Virtual Private Servers (VPS) offer a powerful solution for businesses looking to improve their online presence and streamline their operations.
Explore the benefits of VPS cloud servers and how they can help your business to maximize performance, scalability, and cost-effectiveness. From understanding the basics of VPS to exploring the latest advancements in cloud technology, the knowledge and resources you need to make the most of a VPS cloud server.
Whether you’re a small business owner or a tech-savvy professional, a VPS Cloud Server can help your businesses flourish.
What is VPS Cloud Server?
A Virtual Private Server (VPS) is a type of cloud hosting service that allows a user to rent a virtualized server in a data center. This server functions as a separate physical device but is hosted in a shared environment, providing the user with the benefits of a dedicated server at a lower cost. VPS cloud servers are ideal for businesses and individuals that require more resources and control than a shared hosting plan offers but do not want to invest in the cost of a dedicated server.
In terms of cloud hosting, VPS is considered a “bridge” between shared hosting and dedicated hosting, as it offers more resources than shared hosting but not as much as dedicated hosting.
VPS hosting is typically more expensive than shared hosting, but it is also more powerful and customizable. VPS servers are typically used by small to medium-sized businesses, as well as by individuals who need more control over their online presence.
How does a VPS Cloud Server work?
VPS cloud servers typically come with root access, allowing users to install and configure their software, and are fully customizable, meaning they can be tailored to meet specific business requirements.
VPS cloud servers offer high scalability, meaning that resources such as CPU, RAM and disk space can be increased as needed.
The virtualization technology used for VPS cloud servers is typically either OpenVZ or KVM, which provide different levels of isolation between virtualized environments.
VPS Cloud servers, specifically, are VPS servers that run on a cloud computing platform. This means that instead of being hosted on a physical server, the VPS is hosted on a virtualized environment that is spread across multiple servers. This allows for greater scalability and reliability, as the resources of the VPS can be easily increased or decreased as needed.
Cloud VPS hosting also offers many benefits like automatic backups, easy scalability, and self-healing. These benefits make cloud VPS hosting a popular choice for businesses that are looking for a more flexible and reliable hosting solution.
Considerations while selecting VPS Cloud Server
When selecting a VPS cloud server, it is important to consider the specific needs of a business or project. Factors such as memory, storage, and processing power should be taken into account when choosing a server size and configuration. It is important to choose a reputable and reliable cloud provider, as the uptime and security of servers will depend on the quality of their infrastructure.
VPS cloud server selection comes with many important considerations to keep in mind. The following are mentioned for you to know:
- Performance and scalability: The VPS cloud server should be able to handle the current and future needs of the application. This includes the ability to scale up or down as needed, as well as high performance and low latency.
- Security: The VPS cloud server should have robust security features, such as firewalls and intrusion detection systems, to protect against cyber-attacks and data breaches.
- Reliability: The VPS cloud server should be highly available and have a strong uptime record, to ensure an application is always accessible to users.
- Cost: The VPS cloud server should be cost-effective, with flexible pricing options that allow you to pay for only the resources you need.
- Support: The VPS cloud server provider should offer excellent customer support, including 24/7 availability and fast response times.
- Customization: The VPS cloud server should be customizable to meet the specific needs of the application, whether that includes specific software or configurations.
- Location: The location of the VPS cloud server is also important, as it can affect the speed and reliability of applications. It is best to select a location that is close to the majority of users.
- Compliance: If an application is subject to compliance regulations like HIPAA, PCI-DSS or SOC2, make sure the VPS cloud server provider can meet those requirements.
Now to protect all data running up on the VPS server you need to follow a backup plan too. Let’s read the importance, and types of a backup server.
Importance of Backing Up Both Host Node and Virtual Servers
When virtualizing servers, it’s important to keep in mind that you will need to back up both the host node and the virtual servers. The host node contains the system files that the virtualization software, such as VMware, needs to run. Virtual servers, on the other hand, contain user data that has been created within the virtualized environment. Without a backup of both the host node and the virtual servers, you risk losing important data in the event of a system failure.
Types of Backups for Virtualized Servers
There are several types of backups that can be used for virtualized servers. One option is to have local backups of both the host node and the virtual servers that can be easily restored in case of an emergency. Another option is to use a bare metal backup, which creates a replica of the entire system, including the host node and the virtual servers. Cloud backup solutions can also be used to protect virtualized servers.
Importance of Regular Testing a VPS Cloud Server
Regularly testing backups is crucial to ensure that they can be successfully restored in case of an emergency. This will give you the confidence that virtualized servers can be quickly and easily restored in the event of a system failure, minimizing downtime and data loss.
In conclusion, virtualization has many benefits, but it also brings its own set of challenges when it comes to backups and the selection of one. So do your research and choose wisely.
For more information on VPS Cloud Servers or to configure your own, visit turnkeyinternet.net/cloud-hosted-virtual-servers-vps/
Follow Us :Share :
Dedicated Servers You Can Choose in 2023 no comments

What are dedicated servers
Dedicated Servers (also known as Bare Metal Servers) offer the highest level of service with the ultimate combination of performance, value, and security for your cloud-based hosting needs. Unlike cloud or virtual servers, a dedicated server provides you or your business with exclusive access to all the physical hardware in the server.
Dedicated servers are typically more powerful and reliable than shared servers, which are used by many different customers. They are also far more flexible than other hosting options, giving your organization full control over the security settings, choice of operating system, hardware configuration, and what applications you want to run on the server.
Dedicated servers can be used for a variety of purposes, including hosting websites, running software applications, and storing/managing data.
Application of dedicated servers
There are many practical applications for dedicated servers as their serving of a single network makes them an easy solution to employ. Some of the applications include the following:
• Hosting websites
Dedicated servers are commonly used to host websites, as they provide the necessary resources and stability to handle high traffic. If a website is being hosted on a shared server, then the website may face some performance issues, hence dedicated servers are a better alternative to them.
• Software applications
Dedicated servers can run software applications that require a high level of performance and reliability, such as databases, email servers, and other business-critical applications. For example, big corporations, companies, and hand hospitals have software solutions that require a dedicated server for handling all the related data.
• Gaming
Dedicated servers are used for hosting online gaming competitions. When a large number of players are participating, it requires a server to host a big amount of data.
• Data storage and backup
Dedicated servers can be used to store and manage large amounts of data, and to create backups to protect against data loss. It makes them a handy tool for small organizations.
• Streaming
Dedicated servers can be used to stream video and audio content, such as live events, to large audiences. For example, Netflix and Disney+ have their large-scale dedicated servers to host the data being consumed in large amounts.
• Cloud computing
Dedicated servers can be used to create a private cloud infrastructure for businesses, providing a high level of control over the data and applications being run. Many medium to large-scale corporations use cloud computing solutions so they opt for dedicated servers.
• Machine learning
Dedicated servers can be used to power machine learning workloads, as they provide the necessary resources being fed all the time to train and run complex models.
• IoT
Dedicated servers can be used to process and store data from IoT (Internet of Things) devices such as sensors and cameras and handle communication between devices.
• Virtualization
Dedicated servers can host multiple virtual machines with different operating systems and software, allowing different users to share the same server resources. This is particularly helpful in big offices where employees use different operating systems on their machines.
• E-commerce
Dedicated servers can be used to run e-commerce platforms that handle high traffic and require a high level of security and performance. E-commerce giants Such as Amazon, Alibaba, BestBuy, Shopify, and many others run on dedicated servers.
Factors to consider for choosing dedicated servers
The choice of a dedicated server should be driven by the needs of your business. Although dedicated servers come in a different number of cores and clock speeds, you can choose the number of cores as per requirement. More cores and higher clock speeds, although costs more, will provide more processing power for running high-end tasks such as databases, hosting websites, and running applications.
The RAM factor on dedicated servers is configurable. More RAM will allow for more applications to run concurrently and smoothly. Consider the type and speed of the network connections available on the server. A faster connection will improve performance, especially for tasks such as hosting websites and running applications.
The scalability option is the best solution for whichever dedicated server you choose for your business. A dedicated server that can be easily scaled up or down as per business requirements will be more flexible and cost-effective in the long term.
Enterprise Series Dedicated Servers
TurnKey Internet’s Enterprise Series is a line of enterprise-grade Dell PowerEdge R650xs bare metal servers. The servers are designed for businesses of all sizes and are used for a wide range of applications, including data centers, cloud computing, and high-performance computing. Enterprise Series servers feature the latest 3rd Gen Intel Xeon Scalable Processors, allowing your businesses to easily scale up or down as the needs change.
Enterprise Series servers can be configured with 2 Intel Xeon CPUs and large amounts of memory, allowing them to handle the most demanding workloads. They include a 10 Gigabit Ethernet (10Gbps) network connection and feature a variety of management tools, which allows for easy monitoring, updating, and troubleshooting of the servers.
The Best cPanel Dedicated Server
The Best cPanel Dedicated Server from TurnKey Internet provides the perfect combination of security, performance, features, and cost for the ultimate cPanel Web Hosting Server. This package is perfect for any sized business to host their own website, manage a portfolio of websites, or even resell websites for others as a Reseller or Marketing Agency.
This package offers a complete all-inclusive fully managed service including software licensing for cPanel/WHM, enterprise-grade server backups, and the premium high capacity DEDICATED server with RAID and SSD ultra fast disks.
Conclusion
If you are still unsure which configuration to choose for your business needs, TurKey Internet can help you as we offer many configurations and can provide guidance. To view all of our Dedicated Server options click here, or contact us today to speak with one of our experts!
Follow Us :Share :
Server Location: Why it’s important for your business no comments

What is server location
Server location refers to the physical location of a server. It can be termed as a place where the server is hosted, and the data is stored on those servers. A server or servers are located in a data center, or a co-location facility, or if a corporation is big enough, it can afford to have its server room.Server location refers to the physical location of a server. It can be termed as a place where the server is hosted, and the data is stored on those servers. A server or servers are located in a data center, or a co-location facility, or if a corporation is big enough, it can afford to have its server room.
Importance of server location
Choosing a server location is an important factor if you are conscious of the performance, accessibility, compliance, and especially the cost of a server. The location of a server can have a significant impact on how well it performs, how easily it can be accessed, and how much it will cost to host. There are many other factors when choosing a server location, and one by one they are discussed below.
Latency
Latency is the amount of time it takes for data to travel between the server and the user. The closer the server is to the users, the lower the latency will be. This is especially important for applications that require real-time data, such as online gaming or video conferencing, social media applications, maps, and live streaming. Low latency ensures that users can access the data they need quickly and with minimal delay, which improves the overall user experience and satisfaction.
Bandwidth
The available bandwidth is the amount of data that can be transmitted to and from the server. A server located in a region with better connectivity will have access to more bandwidth. This is important for applications that require large amounts of data to be transferred, such as streaming services or online backups, social media applications, and online games.
Data sovereignty
Some countries are very strict when it comes to data, and they even have enacted laws. The European Parliament has defined data sovereignty as “Europe’s ability to act independently in the digital world”. Therefore, many countries require data to be stored within the very country’s borders. In such cases, the server location should comply with the data laws prevalent in that country. Data sovereignty is a complex issue, and businesses must ensure that they comply with the laws of each country where their data is stored.
Power reliability
Power reliability is an important factor to consider when choosing a server location. Some locations may have more reliable power supplies than others. There are some countries with enough power supplies that even have attracted big corporations to set up servers in their country. Servers rely heavily on power as they need to be running 24/7. A server located in an area with a reliable power supply is less likely to experience downtime due to power outages
Natural disasters
Natural disasters should also be a factor when choosing a server location. Some locations are more prone to natural disasters such as hurricanes, floods, and earthquakes, while some are not. It all depends on the geography and topography of that location This can affect the availability of the server. For example, a server located in an area prone to hurricanes may experience downtime during a storm, which can put people in even double trouble as they can face difficulty in connecting with loved ones and friends.
Climate
Climate is another factor to consider when choosing a server location. Temperature and humidity can have a direct impact on the hardware and cooling of a server. A server located in a region with a cooler climate will have less stress on the cooling system, which can help to improve the lifespan of the hardware. Therefore, most of the biggest servers are located in countries where the temperature is cold or moderate as it also reduces the cost of cooling down the servers.
Cost
Cost is another important factor to consider when choosing a server location. The cost of hosting a server in a particular location varies in terms of logistics and operational costs. Some countries see server locations as less environment friendly whereas some countries welcome them to lure investment. Combining this with the temperature factor, and lower costs for electricity and cooling can help to reduce the overall cost of hosting a server.
Overall, server location is an important consideration when it comes to the performance, accessibility, compliance, and cost of a server. Businesses must consider factors such as latency, data sovereignty, bandwidth, power reliability, natural disasters, climate, and cost when choosing a server location. By carefully considering these factors, businesses can ensure that they choose a location that best meets the needs of their users and their business.
How server location impact websites
Server location can have implications for the website, no matter what sort of website you are running. There are ways where server location affects your website.
Search Engine Optimization (SEO)
Search engines use the geographic location of the server to determine the relevance of a website for specific geographic regions. If your website’s server is located in the same country as the majority of its visitors, it is considered by the traffic engines such as Google, Bing, or Yahoo to be more relevant for that country and may rank higher in search results.
Website Speed
The distance between the server and the users accessing the website can affect the latency, which is the amount of time it takes for data to travel between the server and the user. The closer the server is to the users, the lower the latency will be. This can result in faster loading times and a better user experience for the website’s visitors.
DDoS attack
Distributed Denial of Service (DDoS) overwhelms a server or website with traffic from several sources to render it unavailable. The attack can be lessened, and the website kept online by placing the server in a location with superior DDoS defenses.
Conclusion
Server location can have a significant impact on the performance and accessibility of a website. Factors such as latency, SEO, legal compliance, DDoS attack, and backup/disaster recovery should be considered when choosing a server location. Choosing the right server location can help to improve the user experience.
Follow Us :Share :
Ready to Upgrade? How to Choose the Best Server for Your Business in 2023 no comments

When growing or expanding your IT infrastructure, don’t be overwhelmed by the wide array of server types and options out there. With the right guidance, you can make it a smoother journey. It’s important to focus on critical elements while constructing your ideal server so that it meets all your business needs efficiently.
Understand server requirements
When it comes to running a successful server, performance is key. It’s essential that you consider the hardware specifications required for your setup to ensure smooth operations and maximum efficiency. Consider how many users will be accessing your services along with what those services entail so that you can assess which components best suit their needs – such as hard drive storage, RAM, and power requirements. Planning helps make sure all pieces of the puzzle come together when setting up a functional server!
Server location
Deciding where to locate your server is an essential part of choosing the right one for your business. Careful consideration must be considered when weighing risks, benefits, and costs to make a well-informed decision.
In the ever-evolving field of computing, data centers have become an integral part of companies operating in today’s digital age. Whilst housing a server network onsite may be perceived as more financially effective than outsourcing to remote facilities, there are still several critical factors that should always be taken into consideration when evaluating this route. From energy utilization and maintenance costs to unexpected overtime from employees – having your own data center has its advantages but also comes at certain expenses that you should factor into any decision regarding these vital resources.
Hosting your servers in dedicated data centers not only means you’ll have access to the expert IT support and maintenance that keeps them running, but specialized facilities like backup power supplies help keep them online even when disaster strikes. Keep it cool with optimal cooling and power solutions designed for maximum efficiency, whichever server setup you choose. Take advantage of all these benefits by placing your server networks where they’re given the attention they need: top-notch data centers!
Determine your budget
When you are in the process of setting up a server for your business, it is essential to look at both the immediate and long-term cost implications. It’s not just about what tasks need to be completed today – consideration must also go into future requirements as this could have an impact on budgeting now.
Selecting the right type of server
After taking time and care to understand your budget, technical needs, plans, and more. Now it’s time to select a server that will provide just what you need for your business
Virtual Servers
Virtual servers are an efficient and cost-effective way to provide your company with the necessary computing resources. A single high-capacity server in a data center can host 10 or more virtual private servers, such that each client has privacy protections while still sharing certain amenities like customizable operating systems and software applications across all accounts on a said device–this model provides greater manageability as well!
Dedicated Servers
When you need the most power for your application, there’s no better way than with a dedicated server. This one-of-” kind” service offers all its benefits and more – like increased privacy (you won’t be sharing resources), and custom software designed just for YOU! With less traffic on an idle system thanks to low electricity consumption at night when systems aren’t being used; it will ultimately save money over time due in part to not having as many employees utilize expensive licenses across 3 regions each needing their copy–the savings add up fast
Having considered all the requirements of your business needs, now is when you act and bring home that brand-new server! Get ready to be impressed by just how much more efficient your operations will become with the newest hardware addition at hand.
Not sure what kind of hosting solutions or resources you need? Our team is happy to help you in any way to meet your business needs. Contact TurnKey Internet today and we will help you choose the best hosting solution for your business.
Follow Us :Share :
How To Get Your Website Ready for the Holiday Season no comments

As the holiday season approaches, it’s time to plan and ensure your website is ready for a surge of customers. With some thought and preparation now, you can avoid any technical hiccups that might arise during this busy period. Ensuring customer satisfaction will certainly bring a smile to everyone’s faces – so start updating today!
1. Optimize for Mobile Devices
If you have a website, it’s important to make sure that it’s mobile-friendly. With the growth of smartphones and other mobile devices, online shoppers don’t have to be chained to their computer desks to check off purchases from their holiday shopping lists. Developing a simple and functional theme specifically for your mobile users can increase your potential customer base. The easiest way to do this is to make use of responsive designs. With a responsive design, your website will modify itself automatically to create the optimal layout for the customer’s mobile device; these designs can accommodate both smartphones and tablets. Due to the smaller screen size typical of mobile devices, you probably won’t be able to maintain the same design as your desktop version, but you can still use the same branding and color scheme.
2. Improve Your Website’s Loading Time
Get your website holiday-ready with a few performance tweaks! You may want a website with all the latest bells and whistles but consider your website’s performance before you load it up with high-resolution graphics and elaborate scripts. Sluggish loading times on your website frustrate your customers and may encourage them to shop elsewhere. Before the holidays start, have your technical support team run tests on your website to see how fast each page loads for the average user. Changes to your design, such as reducing large images and eliminating complex coding scripts, can help your website perform better. You can also opt for a better cloud solution or web hosting server for your website to see even more improvement in loading speeds.
3. Secure Customer Data
Shopping online presents unique risks, some websites don’t safeguard customers’ data properly, putting these individuals at risk for identity theft and other issues. Investing in robust security software is a good way to protect your customers’ important data. Your technical support staff should keep apprised of the latest developments in online security to help your customers stay safe. To help alleviate your customers’ concerns, you can include information on your website about the security protocols that you use and offer tips on how your customers can shop online safely.
4. Offer Friendly Customer Support
Browser problems, incorrect stock levels, and missing orders are just some of the common customer issues your staff will need to work through. Make your website ready to tackle the holiday rush by ensuring you have enough staff on hand and that customer service is prepared. . Offer customers a variety of options, including live chat support while they’re browsing, social media engagement in case anyone reaches out there first, or an email ticketing system for those who prefer more personalized communication. Going the extra mile with customer care can make all the difference; proactively anticipate common problems so solutions are already available when needed!
5. Boost Your Search Engine Presence
Get ahead of the holiday rush with improved search engine rankings. Improving your search engine rankings before the holidays begin can help fuel your success during the holiday rush. There are many ways to help boost your search engine rankings, starting with refreshing older pages on your website to give visitors updated material. Offering fresh information to your visitors is a good way to impress search engines and show that your website is active. Adding special features, such as a blog, can also help. If your blog content is particularly noteworthy, you can expect more traffic to head your way. Your blog content should offer something useful to readers, such as tips for using your products.
6. Prepare a Festive Look
A festive design for your website encourages your customers to start thinking about the holidays. You don’t need to spend excessive money on a festive look; changing some pictures and making some cosmetic changes, such as altering the font color, can help dress up your website. Your holiday look should also include banners displaying any specials you plan to run, including discount codes.
7. Brush Up Your Social Media Presence
As the holidays approach, use social media to create a buzz about your products and increase traffic to your website. Don’t let your social media networks sit unused with only a link to your website; update them frequently and interact with your customers. Make sure your profile on each platform matches so that you have cohesive branding. As the holidays draw near, using social media to announce your specials will help you get more interest from potential customers.
8. Beef Up Your Website’s Server
Don’t let large crowds of shoppers ruin your website’s performance when the holidays roll around. If your website is unable to handle massive amounts of traffic at once, a crowd of shoppers on big sales days could lead to sluggish performance or an outright crash. Major server problems are not something to be taken lightly; investing in the right server infrastructure for your expected traffic is a good way to avoid these issues. If your customer base is larger, you might need a dedicated server to keep your website afloat during the holidays. Dedicated Servers may cost more than basic shared or cloud hosting, but your website won’t be at the mercy of problems caused by other websites/users on the server.
Examining every aspect of your website before the holidays arrive can help you prepare a strategy to improve customer satisfaction and your business’s success. A good website requires many things, including fast loading times, quality customer service, and security. Working on these elements early can ensure that your website is ready long before your customers even start to think about tackling their holiday shopping lists with your business.
Follow Us :Share :
A Beginner’s Guide to Choosing the Right Web Hosting Solution no comments

Businesses are converting their IT infrastructure into the cloud every day – phone systems, virtual desktops, and office servers. But when your business makes that transition to The Cloud why do you need so many options that look similar but have different names like “Cloud Hosting” or “Virtual Servers”? Which type is best for you– and what’s in between?
The Cloud
“The Cloud” is one of the most popular terms on today’s internet but lacks an agreed-upon universal definition. The cloud offers scalability and reliability at a low cost; it can be accessed from anywhere with an internet connection via various technologies such as Voice over Internet Protocol (VoIP) telephone calls or video conferencing applications which use WebRTC.
Virtual Servers
Virtual servers are an efficient and cost-effective way to provide your company with the necessary computing resources. A single high-capacity server in a data center can host 10 or more virtual private servers, such that each client has privacy protections while still sharing certain amenities like customizable operating systems and software applications across all accounts on a said device–this model provides greater manageability as well!
Dedicated Servers
When you need the most power for your application, there’s no better way than with a dedicated server. This one-of-” kind” service offers all its benefits and more – like increased privacy (you won’t be sharing resources), and custom software designed just for YOU! With less traffic on an idle system thanks to low electricity consumption at night when systems aren’t being used; it will ultimately save money over time due in part to not having as many employees utilize expensive licenses across 3 regions each needing their copy–the savings add up fast
Cloud Hosting
Cloud Hosting can mean just about any type of hosted solution in a secure data center. The more advanced Cloud Hosted solutions providers are offering a robust scalable network of servers that can provide redundancy and scalability that otherwise is not present in a single virtual server or dedicated server. You must be careful when you shop for vendors who use the term “Cloud Hosting” to promote using the Cloud to host your application or server. What you generally want is a cloud hosting solution that offers you a ‘virtual machine’ in the cloud provider’s network, that offers some level of scalability, and redundancy.
TurnKey’s offering
TurnKey Cloud offers a full virtual machine on top of multiple redundant clusters of servers which provides the cloud benefits of scalability and redundancy to let you install any operating system and any applications without having to utilize software developers to convert their applications to a proprietary cloud platform. If it runs on the server in your office, it will run in the TurnKey Cloud platform.
Follow Us :Share :
TurnKey Internet Launches Latest 3rd Generation Intel Xeon Scalable Processors no comments

ALBANY, NEW YORK – November 3, 2022 – TurnKey Internet, a ColoHouse company, launches the latest 3rd Gen Intel® Xeon® Scalable processors in its dedicated server, new cloud offering in existing locations, Albany, NY; Orangeburg, NY; Colorado Springs, CO, and adding new server footprints into Chicago, IL; Miami, FL and Amsterdam, The Netherlands.
With these new upgrades, TurnKey Internet, is introducing their all-new Enterprise Series Dedicated Servers, Dell PowerEdge R650xs, powered by the latest 3rd generation Intel® Xeon® scalable CPUs. Built to handle the most complex and demanding workloads, the new capabilities feature flexible performance, AI acceleration, higher memory bandwidth, enhanced security and data protection, and can be configured with high performance NVMe drives. Each server is directly connected to a dedicated 10 Gbps network port featuring premium Tier-1 bandwidth powered by TurnKey Internet.
“Based on feedback from our clients and the expanding workload of applications, we delivered a new dedicated server product line designed to exceed the current and future demands of our fast-paced customer base,” says Adam Wills, SVP of Hosting Solutions at ColoHouse. “Customers are creating agile and mission-critical environments that require 24/7 multi-cloud, multi-geolocation and Availability. With the 3rd Gen Intel® Xeon® Scalable processors, TurnKey Internet has built upon the existing global data center footprint and solid dedicated server automation foundation to provide best-in-class enterprise features. These include automation, flexibility, security, speed, efficiency, and most importantly, performance that our customers’ workloads demand.”
“TurnKey Internet’s rollout of the latest generation of Dell servers offered to customers in existing and additional locations in the ColoHouse portfolio is the exciting result of integration efforts since the acquisition a year ago. Servers in all of our US locations are now available and servers will be available for purchase in The Netherlands in early 2023.” says COO of ColoHouse, Kyle Verzello.
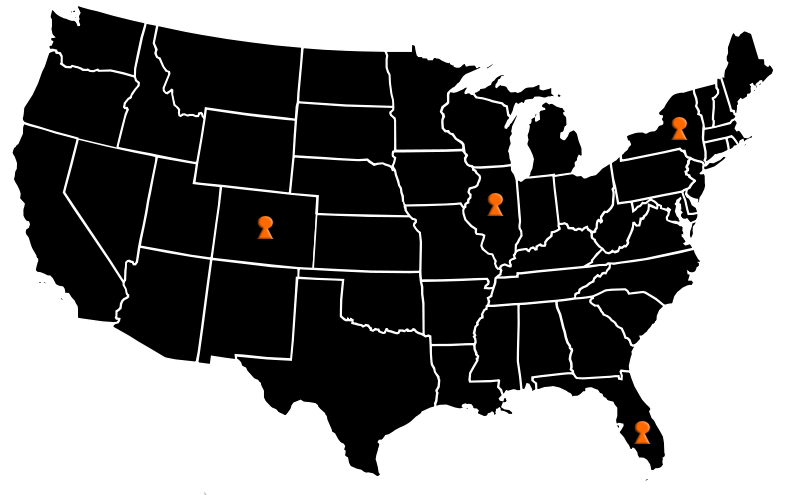
New York, Miami, Colorado Springs, Chicago, and The Netherlands are all operated and managed by ColoHouse, which acquired TurnKey Internet in November 2021. In conjunction with this 3rd generation rollout, TurnKey Internet will begin its annual Black Friday sale, available on its website.
Click here to learn more about TurnKey Internet’s Enterprise Series Dedicated Servers expansion and Black Friday Deals.
About TurnKey Internet:
Founded in 1999, TurnKey Internet is a full-service IT Hosting Solutions provider specializing in Infrastructure as a Service (IaaS) to clients in more than 150 countries. Services offered include Cloud Hosting, Dedicated & Bare Metal Servers, Backup & Disaster Recovery, Online Storage, Web Hosting, Managed Hosting, and Hybrid Solutions. Headquartered in New York’s Tech Valley Region, TurnKey Internet takes pride in its customer focused 5-star experience that exceeds expectations by delivering outstanding quality, reliability and value. TurnKey Internet always puts the customer experience first. TurnKey Internet is a ColoHouse Company. For more information, please call (518) 618-0999 or visit www.turnkeyinternet.net.
Follow Us :Share :
Cloud or Dedicated Servers – What’s The Difference? no comments
Today’s businesses have several options available when it comes to hosting. Cloud hosting services have become increasingly popular, yet dedicated servers continue to offer the greatest flexibility and customization.
Are you confused about your options regarding cloud computing and dedicated hosting for your business? You need to understand each server type to choose the right one for your business.
Cloud Hosting
Cloud hosting has become increasingly popular in recent years as businesses have looked for efficient and secure ways to store, manage and process their data. The cloud is the delivery of on-demand computing resources over the Internet. A cloud server is a virtual server running in a cloud computing environment. A business migrates its data and applications from its physical servers into the cloud provider’s virtualized servers. Cloud hosting is an ideal solution if you want to enhance your IT performance without incurring huge costs on purchasing infrastructure.
Dedicated Server Hosting
Dedicated servers are known for their high-performing features in processing power and storage speed, are connected to high-speed internet connections, and are hosted in data centers. Dedicated servers can be used for any number of things, some of which is the hosting of websites or database-intensive applications. A good example of this could be CRM systems such as Microsoft Dynamics or SAP. As the name implies, each server is dedicated privately to one customer. That customer receives access to a physical server with the agreed-upon hardware specifications, processing, and storage, all in one unit.
Cloud vs Dedicated Servers
Determining which applications are best suited for your business, whether dedicated servers or cloud hosting, you must keep in mind what requirements and security measures are needed to create the most effective and efficient infrastructure for your business.
What should you consider before choosing a server for your business?
- What are your long-term goals?
- What are your IT requirements?
- What is you budget?
Once you have verified that a server meets your functional requirements you must also make sure you are not paying for anything you will not utilize.
Your primary concern is: What problem do you want to solve?
Hosting Solutions
Not sure what kind of hosting solutions or resources you need? Our team is happy to help you in any way to meet your business needs. Contact TurnKey Internet today and we will help you choose the best hosting solution for your business.
Follow Us :Share :
When Do You Need a Dedicated Server? no comments

With the ever-growing need for IT resources, many businesses are turning to dedicated servers as they offer a powerful way of hosting. But how do you know if this is the right choice?
A great start would be assessing your current situation and seeing where any pain points arise that could use some attention from our team!
What is a Dedicated Server?
A dedicated server is a single physical server, housed in an off-site data center that is entirely dedicated to one user or organization. These servers are known for their high-performing features in processing power, storage speed, and connection to high-speed internet. If your business needs a large amount of processing power, then a dedicated server is the right choice.
How to know when you need a dedicated server?
Backup solution
Planning and implementing your IT infrastructure is one of the most important decisions you will make for your business. Backing up your critical data is a simple and essential step in protecting your business. A proper backup and data storage solution along with full business continuity and disaster recovery plan, work together to reduce threats to your business. A server can function as a secure environment for mission-critical data and more.
Flexibility
As your business expands, dedicated servers can accommodate your growing business needs. Compared to other hosting options, dedicated servers give you ultimate flexibility and resilience. Dedicated server hosting enables businesses to control resources without any restrictions and can be upgraded or scaled back easily within the limits of your contract.
Security
The key advantage of dedicated servers is security. Since you are not sharing resources with other users; it is for your exclusive use only – the security of your server is entirely in your hands. Controlling what happens with your server’s operating system and its applications puts you in the driver’s seat. You won’t need to worry about other users and their potentially outdated applications or bad code. An off-site dedicated server in a secure data center will protect your server from power outages and any other physical harm (robbery, flooding, etc) in addition to having 24/7 support vs an on-premises server.
Performance
A dedicated server is entirely dedicated to you and you alone. This means that users of a dedicated server do not have to share any of its resources with other users. Your dedicated server will give better performance. This way you can enjoy the best of both worlds when it comes to hosting as the performance and reliability are not impacted by others.
When deciding which hosting solution to go ahead with, it is essential to consider your business needs, and how much it’s likely to scale shortly. So, what works best for your business? Contact TurnKey Internet today and we will help you choose the best hosting solution for your business.
Follow Us :Share :
Top 3 Reasons Why You Need a Dedicated Server no comments

The flexibility and scalability of cloud computing have transformed the IT industry, but there are still times when the stability, control, and performance power of a Dedicated Server may be the solution you need for your business.
With a Dedicated Server, your business has exclusive use of that server’s resources. You also have the flexibility of customizing the server’s CPU, RAM, and disk space based on the needs of your business.
What is a Dedicated Server?
A Dedicated Server is a physical bare metal server with dedicated resources, including CPU, RAM, storage, and network ports. A Dedicated Server has been dedicated to a single tenant. In other words, it’s not shared with anyone else. This contrasts with virtual servers, which are created using virtualization software and can be shared by multiple tenants.
Here are 3 top reasons why you should choose a Dedicated Server:
No Shared Resources
Dedicated servers dedicate all computing resources to a single user. Every bit of power, storage, and bandwidth is exclusive to you and no one else. Not only will this give your business more room to work with and expand, but it will also prevent issues with your site caused by other websites.
Custom-build your ideal environment
Dedicated servers allow your business to customize the hardware and software based on your business’s unique needs, including server configurations, RAM, SSD hard drives, bandwidth options, and more. With shared hosting, you are limited to the software already installed on the server, and sometimes it may lack a requirement or feature your business needs. But with a dedicated server, you have full flexibility over which software the server runs, even down to the Operating System.
Security
Dedicated servers offer improved security. Your physical hardware is isolated from other servers and their tenants, eliminating any potential risks of data breaches and other cyber-attacks
Choosing a solution
Now if you’re worried that you’re not tech savvy enough to run your own dedicated server, consider the option of going with a Managed Dedicated Server solution, which will provide many additional benefits on top of what’s listed above. Before you decide to host your website on a shared server, consider the added flexibility, reliability, and performance that only a dedicated server can provide. Contact TurnKey Internet today and we will help you choose the best hosting solution for your business.
Follow Us :Share :



