Archive for the ‘ransomware’ tag
Ransomware 2.0 – Are your servers safe? no comments

Are your servers safe from the latest evolution of malware – Ransomware 2.0? You better hope so or else you will pay the price, literally.
What is Ransomware?
The frequency of ransomware attacks has increased dramatically over the past year, with 93% more carried out in the first half of 2021 than in the same period last year, according to Check Points mid-year security report.
Ransomware primarily began through email and malicious ads. However, this new breed of ransomware is targeting network and server-side vulnerabilities, with the ability to self-propagate. It will be able to quickly switch methods to maximize efficiency and will evade detection by limiting CPU usage to refrain from command-and-control actions.
Ransomware 2.0 “will start replicating on its own and demand higher ransoms. You’ll come in Monday morning and 30% of your machines and 50% of your servers will be encrypted. These new ransomware strains will spread faster and self-replicate within organizations before coordinating ransom demands. It is critical that companies take the needed steps to prepare and protect their network as well as their local and cloud-based servers.
How to protect your business from ransomware?
Now you may be wondering “What steps should I take?” Well, we’re glad you asked! The key is in taking a proactive approach to prevent rather than remediate. There are some easy yet vital best practices you should follow to protect yourself.
First and by far the most important, back up your data. Second, consistently keep your software and systems up to date. Third, make sure you are utilizing some form of antivirus and malware protection software on your PCs and servers. Finally, back up YOUR DATA! Yes, we know we said that already, but this step is so critical it’s worth mentioning twice. If you don’t currently have a backup solution, TurnKey Internet has multiple cloud-based disaster recovery and backup solutions to choose from, such as R1Soft Continuous Data Protection.
To learn more consider using these four best practices for backing up your data.
Your primary goal is to protect your users, not just your network. Whether they are on a laptop, tablet, or smartphone, your users need to be protected everywhere. However, it is unreasonable to assume that you will be 100% protected from every threat that exists. New more advanced methods to attack computers and encrypt their files are popping up every day. Therefore, your number one priority should be to back up your data regularly. If that moment comes where you find yourself infected with ransomware, the comfort of knowing your data is backed up, safe, and secure is priceless. However, if you chose not to back up your data… be prepared to pay the price.
Find out how TurnKey Internet can help protect your business against ransomware and other threats, securing you today and tomorrow. Visit www.turnkeyinternet.net/myplan for a FREE consultation!
Follow Us :
Share :
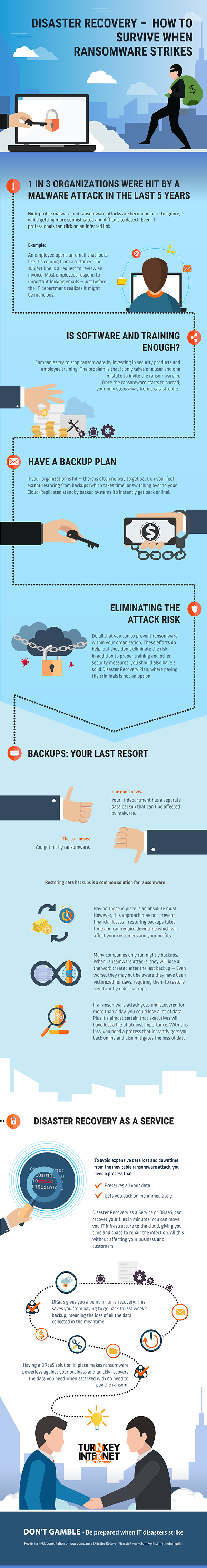
Disaster Recovery – How to Survive When Ransomware Strikes (Infographic) no comments
DON’T GAMBLE – Be prepared when IT disasters strike
Receive a FREE consultation of your company’s Disaster Recovery Plan, visit www.TurnKeyInternet.net/myplan
Ransomware, Careless Employees, and IT Gremlins – Better Have Backups no comments
From buying insurance policies to installing security cameras, you take every possible step to protect your business from disaster. But you power on your computer and are met with a screen that claims to have encrypted all of your files. Unless you pay a fee before the timer expires, the program will delete your files forever. Although each situation will be different, this is what will likely happen when ransomware strikes your business.
If you store your customer data, tax information, contracts or any other important files on your network, your business can suffer. Not only will ransomware lock your files, but it can also destroy your reputation if your customers find out that your servers are not secure. When the future of your business is on the line, you can’t afford to leave yourself exposed to the threat.
Taking preventative steps to minimize the effects ransomware is a lot easier than trying to remove it. Once the ransomware takes over a computer, you won’t be able to recover your files without paying the ransom. To ensure your business is ready for a ransomware attack, you should focus on some key areas:
Employee Education
Criminals and hackers will use a range of tactics to infect a business or organization with their malicious software, including sending an email containing an infected link to one of your employees. The infected email can even be made to appear as if it came from one of your company’s email addresses. The moment your employee clicks on the link, the ransomware will jump into action and hold your files hostage. Also, if a member of your team is infected at home and brings a flash drive to work, you could have a problem on your hands.
Teaching your employees how to stay safe online is one of the top ways to protect your business from such attacks. If you want to avoid taking unneeded risks, prevent your employees from using personal devices on your network. Ensure that each person who works for you knows not to click on links unless they are sure that no danger is present. When someone from your company sends an email, have your team call the person to confirm that the email is legitimate. In addition to showing people how to stay safe when they use your network, consider putting policies in place to add an extra layer of protection.
Cloud Backups
Ransomware can easily spread across your office network, encrypting and possibly deleting all of your company’s files. If you want to do everything that you can to avoid such a disaster, consider getting an off-site dedicated server or cloud backup solution for your business. Doing so will allow you to store copies of your files outside of your infected office network, so that you can recover them after an attack.
One thing to keep in mind when searching for a cloud backup provider is storage limits. If your business has a large amount of data that will need to be backed up into the cloud, consider looking for a provider that offers an unlimited storage option.
Disaster Recovery as a Service (DRaaS)
No matter how prepared, you can never totally eliminate the threat of ransomware. Even if you have taken the step to backup all of you company’s critical files, you can still be left with the daunting task of restoring all that data as well as needing to recover your company’s entire IT infrastructure. This is where Disaster Recovery as a Service or DRaaS comes in.
With a DRaaS solution, you can have a complete backup of your business’s vital IT infrastructure at an off-site datacenter. Entire operating systems, whether it be physical or virtual, databases or individual files and folders can all safely and securely be replicated to a datacenter. Data can then be securely pushed back down to your office location, or it can even be restored into a virtual cloud environment, utilizing Cloud Replication.
Cloud Replication
DRaaS solutions that feature Cloud Replication allow for the restoration of data to a virtualized server. Utilizing an off-site datacenter’s cloud infrastructure, data can be made available instantly, then accessed remotely from anywhere in the world over multiple, redundant, high speed networks. This removes the bottleneck of local internet service providers bandwidth availability, and saves potentially hours of business critical time by bypassing the need to wait for your onsite systems to restore and be back in working order.
Should a disaster occur in which your infrastructure is no longer available or accessible to be restored, the need to purchase new hardware can be completely eliminated. Utilizing a DRaaS solution can have your business back online in minutes, not days. Employees can continue their work from home, remotely accessing images of their old workstations running live in the cloud, ensuring your business does not skip a beat.
Be Prepared When IT Disasters Strike
TurnKey Internet is Upstate New York’s only Tier IV featured Data Center providing 100% Guaranteed Uptime. We offer Colocation, IT Infrastructure, New York to California replication, on-premise 24×7 expert local staff, and the Cloud solutions to help your business succeed.
TurnKey’s DRaaS (Disaster Recovery as a Service) solution offers live Cloud Replication for your on-premise IT infrastructure to our Tier IV featured Data Center in a secure virtualized hybrid environment that is instantly available and securely accessed remotely from anywhere.
Don’t gamble, call TurnKey Internet at 518-618-0999 or visit turnkeyinternet.net/myplan to receive a FREE consultation of your company’s Disaster Recovery Plan.
What is Ransomware? no comments
Over the past few years malware infections have seen an exponential growth. They are becoming more sophisticated, using newer methods that are not only harder to detect, but also require less user interaction. One of the more prominent forms of malware, especially in recent days, is called Ransomware.
Ransomware is form of malware, or malicious software, that carries out its attack by encrypting the data on a computer or server, then blocking access to that data until a ransom is paid.
Security researchers report attackers are not only upgrading their ransomware to make it more unbreakable, they are also using unique methods of distribution. In some cases, these methods require no user interaction at all. In the past, most ransomware infections occurred via phishing attacks, which required a user to click on a malicious website or email link. But these newer attacks are less dependent on user interaction and more dependent on unpatched software or Operating System vulnerabilities or poor security practices.
Ransomware is spreading faster and is self-replicating within organizations and businesses before coordinating ransom demands. It is critical that companies take the needed steps to prepare and protect their network as well as their local and cloud-based servers. The damage of ransomware encrypting and disabling all of your corporate data within seconds or minutes is real and has lead to some high profile cases including hospitals being locked out of all their data due to ransomware.
There are some easy yet vital best practices you should follow to protect yourself and your company from becoming victims of ransomware. First and by far the most important, backup your data. Second, consistently keep your software and systems up-to-date. Third, make sure you are utilizing some form of antivirus and malware protection software on your PC’s and servers. Finally, BACKUP YOUR DATA! Yes, I know I said that already, but this step is so critical it’s worth mentioning twice. If you don’t currently have a backup solution, there are many cloud-based disaster recovery and backup options to choose from, such as TurnKey Vault.
Your primary goal is to protect your users, not just your network. Whether they are on a laptop, tablet or smartphone, your users need to be protected everywhere. However, it is unreasonable to assume that you will be 100% protected from every threat that exists. New more advanced methods to attack computers and encrypt their files are popping up everyday. This is why your number one priority should be to backup your data regularly.
Make sure whatever backup solution you deploy offers data encryption, supports both desktop PC’s and Macs, as well as Linux and Windows based servers. A backup solution like TurnKey Vault offers live cloud replication which will get you back on your feet in minutes in case of a true disaster by creating a live cloud-based copy of any PC workstation or Server accessible from anywhere over the Internet to get you access to your data and applications quickly.
It’s 2016 – Is Your Office Server or Web Site Being Held Hostage? no comments
 The latest wave of computer security news may sound like the headline of a new Bruce Willis movie – but Ransomware is now part of the daily conversation between not only security experts, but unfortunately by office managers and PC users across the globe having to deal with the ramifications.
The latest wave of computer security news may sound like the headline of a new Bruce Willis movie – but Ransomware is now part of the daily conversation between not only security experts, but unfortunately by office managers and PC users across the globe having to deal with the ramifications.
This year malware infections, more specifically ransomware, have seen an exponential growth. They are also becoming more sophisticated, using newer methods that are not only harder to detect, but also require less user interaction.
Security researchers report attackers are not only upgrading their malware to make it more unbreakable, they are also using unique methods of distribution. In some cases, these methods require no user interaction at all.
In the past, most ransomware infections occurred via phishing attacks, which required a user to click on a malicious website or email link. But these newer attacks are less dependent on user interaction and more dependent on unpatched vulnerabilities or poor security practices.
These new breeds of ransomware are utilizing more advanced methods to attack computers and encrypt their files, before you even realize what’s happened. You are then forced to either pay the ransom or hope you have a backup recent enough to prevent any lost data.
To protect yourself you need to follow best practices, such as
- backup your servers and PC’s
- backup your servers and PC’s
- see item (1) and (2) above (seriously!)
- keep your software and systems patched and up-to-date
- Have a corporate gateway firewall with advanced threat protection
- Have / Install / Update local AntiVirus and Malware Software protection
- Always avoid opening un-expected emails or attachments
- Avoid clicking to web sites you don’t recognize (especially if sent in email)
- if you aren’t backing up your servers and PC’s already – stop reading and visit https://turnkeyvault.com/
It’s pretty simple – the same things that protect your office data and servers from most threats apply here, but the damage of ransomware encrypting and disabling all your corporate data within seconds or minutes is real and has lead to some high profile cases including hospitals being locked out of all their data due to ransomware! Don’t let your business fall victim to the bad-named villain of a Bruce Willis movie – ransomware is among the most costly cyber threats actively attacking businesses right this very second.
Make no mistake – backing up your data is a must have in any security policy, and utilizing a secure remote cloud based backup solution such as TurnKey Vault is ideal. Make sure whatever backup solution you deploy offers data encryption, supports both desktop PC’s and Macs, as well as Linux and Windows based servers. A backup solution like TurnKey Vault offers live cloud replication which will get you back on your feet in minutes in case of a true disaster by creating a live cloud-based copy of any PC workstation or Server accessible from anywhere over the Internet to get you access to your data and applications quickly. If ransomware takes over your office network you can spin up a backup live copy of your servers and PC’s with TurnKey Vault from a time before the ransomware took over your office – and will have you saying “Yippee Ki-Yay” just like Bruce Willis as the ransomeware data hostage takers wont ever see a dime, and you will have all your data safe and secure.