Archive for the ‘spam’ tag
reCAPTCHA: digitizing the printed word, one spam filter at a time 7 comments
 In 2009, Google went from having around 20,000 employees, to having millions of people all over the world working for them. Well… sort of.
In 2009, Google went from having around 20,000 employees, to having millions of people all over the world working for them. Well… sort of.
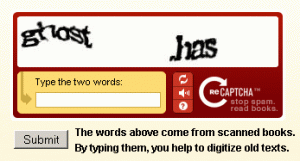
You might already be familiar with what is pictured below. If not, let me explain to you a little bit about something that I was recently informed about –this magical thing called “reCAPTCHA”.
 In the year 2000, I was worried about passing the 4th grade. I was anticipating that all the computers in the world were going to explode due to Y2K. I was hoping that I could fend for my family and not die of Dysentery on The Oregon Trail. Needless to say, life was rough.
In the year 2000, I was worried about passing the 4th grade. I was anticipating that all the computers in the world were going to explode due to Y2K. I was hoping that I could fend for my family and not die of Dysentery on The Oregon Trail. Needless to say, life was rough.
But Yahoo!—and hundreds of other web companies, for that matter—were dealing with a much larger epidemic than Dysentery—spam. No, not that gross, canned mystery meat, and definitely not George Michael’s Wham! This kind of spam is something (debatably) worse than both… combined!
We’ve all encountered spam in our email inboxes, but now, thanks to Luis von Ahn, we also have all run into what is stopping most of it.
Luis von Ahn grew up in Guatemala and worked in his family’s candy shop as a kid. Later on in his life, along with his college advisor, he was hired by Yahoo! to create a program that could tell the difference between a human and a form bot. They came up with “CAPTCHA”, which—and I’m serious here—stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.”
While the name isn’t exactly the work of genius, these brilliant guys created a challenge-response test that could be predominantly passed by humans to block those evil form bots and eliminate as much spam as possible. These computer-generated, squiggly words are made so humans can read and submit them, but that computers cannot.
After becoming extraordinarily successful off this creation, Mr. von Ahn still found a weakness in his own program. The flaw? The 10 annoying seconds wasted while someone types in a CAPTCHA every time they come across one. After turning down a personal offer from Bill Gates to work for Microsoft and winning the MacArthur Fellowship Award in 2006, von Ahn re-created CAPTCHA and titled it…erm… reCAPTCHA! Luis von Ahn believed this new idea would be good for humanity, and as far as some other types of crowdsourcing go, I agree.
In 2009, Google bought reCAPTCHA and released it upon the masses. Now, what reCAPTCHA does is take the words we type in and use them to digitize old books and newspapers. These books and newspapers are scanned and turned into text-images by using “Optical Character Recognition” (OCR). The problem remains that computers still cannot read text as well as humans. A simple word like “of” could be interpreted as “at,” since old books and newspapers may have words that are damaged or hard to scan.
Here is where the superpower of humans comes in! We can read the word “of” and correctly submit “of,” instead of “at”, along with a computer-generated CAPTCHA word. So a reCAPTCHA image is combined with a CAPTCHA word, and placed at the login of something like an email. If we get the CAPTCHA word correct, we are in-there-like-swimwear. Even if we get the reCAPTCHA wrong and cannot decipher it ourselves, but get the CAPTCHA, we are still allowed access. The reCAPTCHA word will be tested by many other humans to increase the likelihood of it being deciphered correctly.
Using the aforementioned example of the word “of” being read as “at”, if people keep typing “of”, the word “of” will digitally replace the word that the OCR program recommended. After some time, millions of people are deciphering these scanned reCAPTCHA words and creating digitized versions of old New York Times newspapers and classic books for Google!
In months, with the power of reCAPTCHA and humans’ ability to read damaged words, 20 years’ worth of material is digitized and transcribed thanks to… well… you…me… Alan Rosenberg… maybe Luis von Ahn and Bill Gates… your mom? Everyone! In time, thanks to Luis von Ahn and his team, we will all be a part of digitizing millions of old texts to be distributed online. Now, where are our paychecks, Google?
Follow Us :Share :
Stop Spammers From Abusing Your Web Hosting Server no comments
Today, spam is a fact of life. Because of the daily spam deluge (and those over-zealous anti-spam systems) many email communications require a follow up phone call… “did you get my email?”
You may not realize it, but if you send emails through your web hosting server or virtual server and operate a web hosting business, web development business or host your email with a web hosting company, you have likely had some trouble getting your emails through. Often the reason is that your server has been used to send spam without your knowledge. Most of today’s web hosting companies employ automated protection to stop such things, and catch abuse before it gets out of hand. But spammers are getting more clever and an increasing number of stealth spamming techniques can bypass these systems.
Many web hosting companies resell web hosting, and their resellers (unbeknownst to them) send out spam. This can result in the blacklisting of the entire server, and everyone on it, which will keep most (if not all) emails sent from the server from ever reaching their destinations. Of course, it is the web host’s responsibility to carefully monitor their clients and web sites on their server(s) to make sure this never happens. Traditionally, this hasn’t been too difficult. Today’s modern web hosting systems employ advanced abuse tracking and header info in every email making it easy to catch and stop this type of abuse before it becomes a problem.
Lately, however, this has become a lot harder. There is a new wave of spam abuse that hides under the radar, bypassing the web server’s normal email system(s) by opening up a small cgi program, which then operates as a small mail sending server, which then floods spam out onto the Internet. Unfortunately, none of the traditional monitoring systems are able to detect this sort of stealth spamming. Naturally, for this reason, it has become very popular.
Fortunately, here at TurnKey, we’ve figured out a fix for web hosts and developers using cPanel (this will work on other servers, such as Plesk and DirectAdmin as well). Our fix will stop stealth spam dead in its tracks! Until it is a built-in a feature in all hosting companies’ server offerings, make sure you ask your web hosting company to set this up for your server. Alternatively, you can pick a web hosting company that takes care of it themselves (like TurnKey Internet).
First, login to your cPanel server via the unix shell and install CSF firewall. Follow the usual instructions here:
mkdir /usr/local/src
cd /usr/local/src
wget http://www.configserver.com/free/csf.tgz
tar xfz csf.tgz
cd csf
./install.sh
On a cPanel based server, all the default settings are what you want, with 2 exceptions:
Open the configuration file in your favorite text editor (/etc/csf.conf) and change the following lines:
TESTING = “1” change to TESTING = “0”
NEXT: you need to change 2 more lines, the SMTP_BLOCK and SMTP_ALLOWLOCAL to the following values:
SMTP_BLOCK = “1”
SMTP_ALLOWLOCAL = “0”
This will block outbound emails from anyone other than the mail server software, and prevent any unauthorized access to the mail daemon from local scripts. Your web hosting clients, and web pages will still be able to send email like before (they use a proper method of communicating to the mail daemon already, this above trick is just to block stealth spammers from working).
restart the firewall by typing:
/etc/init.d/csf restart
If all goes well your server will now be protected by a firewall with an added check to prevent spammers from sending emails that avoid the normal php_mail or other local mail sending method (which lets you track and log all emails, put in abuse headers by default, etc.).
Next time on Ask the Expert, we will show you how to optimize your server to really cut down on abuse from spammers.
Follow Us :Share :



