Archive for the ‘wordpress’ tag
10 Essential WordPress Security Tips no comments
Failing to protect your WordPress site from potential hackers could leave years of work vulnerable to attack. Malicious users know how to exploit vulnerabilities in unprotected sites, hijack files and plugins for their own use and sabotage functionality.
If you’re not doing all you can secure your site against attacks, it’s time to take action. Use these ten WordPress security tips as a starting point to lock out hackers and protect your web presence.
1. Obscure the Login Page
By default, WordPress users access their login pages via domain names followed by wp-login or wp-admin. Hackers know this and will immediately navigate to these pages when attempting to enter your site. Using a security plugin, you can change the URLs of login and user registration portals. Although this doesn’t prevent hackers from eventually finding these pages, it slows them down and may be frustrating enough to make them give up trying to access your site.
2. Choose Unique User Identification
Using “admin” as your administrator login name is like an open door for hackers. Your login should be distinct to your website and difficult to figure out. One way to ensure your login remains unique is to use the email associated with your WordPress installation instead of a username. Email addresses are harder to guess and offer better authentication for administrator logins.
3. Be a Password Juggler
There was a time when you could stick a few numbers on the end of your dog’s name and call it a reliable password, but in today’s volatile Internet landscape, you need much more than that. Use a password generator to create strong WordPress passwords, and change them on a regular basis. Good passwords include uppercase and lowercase letters, numbers and symbols in various combinations. The more complex your passwords, the more secure your site will be.
4. Enable Two-Factor Authentication
Many sites employ a two-step process to verify the identity of each user attempting to log in. Using the same method on your site means it will take a little longer for you to get to the dashboard, but it may prevent hackers from gaining access to your site. Two-factor authentication lets you choose a secret question or a special code to be after the initial password screen. Some methods use a one-time authentication message sent via text to ensure only authorized users can log in.
5. Install a Security “Watchdog”
Hackers need multiple attempts to get into your WordPress site, and plugins like WordFence alert you to this activity while locking down the site to prevent unauthorized access. Such security plugins act like gatekeepers, watching who tries to log in, sending alerts, checking for file changes and banning offending IP addresses. Reports of activity arrive in your inbox immediately and again in weekly summaries so that you can keep on top of any potential problems.
6. Control Other Accounts
Collaborative or corporate blogs require several user accounts, and this can pose a problem for security unless all users understand how to keep the site protected. Be selective when adding accounts, since every new login creates another potential point of vulnerability. Establish rules about password strength and how frequently passwords should be changed, and make sure each user has a distinct login name. Set individual user permissions at the lowest levels possible so that it’s difficult for hackers to do damage should additional accounts ever be compromised.
7. Use .htaccess to Hide Important Files
Editing the .htaccess file can change certain WordPress functions, including the level of security. With the right code, you can:
- Disable directory listings to prevent unauthorized users from accessing file listings
- Hide your wp-config file from malicious users
- Set which IP addresses are granted administrative privleges
- Block access to the PHP files for themes and plugins
Remember to back up the existing .htaccess file before making any changes.
8. Stay on Top of Updates
Themes, plugins and the WordPress core are updated regularly to fix known problems, including security issues. Before installing any plugin or theme, check the last time it was updated. Ensure the developers offer continued updates after installation, and stay away from pirated “free” versions of premium plugins.
Run updates as soon as you can to eliminate vulnerabilities. If you have trouble remembering to update or have a tendency to miss notifications, consider setting automatic updates to run on a routine basis.
9. Don’t Neglect “Spring Cleaning”
Make a habit of going through the plugins and themes stored on your WordPress site whenever you run updates. Delete anything you haven’t used in a while or have replaced with something more functional. You may be surprised how many plugins you’ve accumulated while building your site, and getting rid of unused ones eliminates vulnerabilities.
It’s also a good idea to clean up your database from time to time. Find a reliable database cleaning plugin and run it to remove old file versions and other outdated information. As a bonus, your site should load faster and run more smoothly without the extra files weighing it down.
10. Backup as Often as Possible
No matter how careful you are, there’s always a chance an enterprising hacker could break through your site’s defenses. Creating site backups safeguards all the information on your site, giving you a way to restore everything should your security measures ever fail.
Some hosting companies provide scheduled backups as part of their services, but it’s a good idea to also have your own plan in place. Use a backup plugin or make manual backups on a regular basis, and store the files in a secure place so that you know they’ll always be there if you need them.
WordPress site security isn’t a “set it and forget it” measure. After putting initial protections in place, it’s essential to continue monitoring activity and running updates. Keep an eye out for new, stronger security tools, and implement the best combination of plugins and code changes to prevent the majority of attacks.
Follow Us :
Share :
Effective Security Measures For Your Server no comments
If you run a server, especially for your business or organization, security should be a top priority. Whether the server exists to host files for a website or is networking computers for an office, it needs to be protected from malicious software, exploits and hackers. Failing to secure a server can lead to lost or corrupted data, damage to devices connected to the network and unauthorized individuals getting access to sensitive data. Below are various security measures that you can employ on your server that are extremely effective.
Review & Modify Default Settings
Programs running on your server, such as control panels (cPanel, Plesk), CMS (WordPress, Joomla, etc.) and even the operating system, contain various default settings that need to be reviewed and if necessary modified. They include everything from preset usernames and passwords for admin access to default connection ports. Anything that is left as set up by the software manufacturer may be used as a way to gain easier access to a system. Even leaving the URL for admin access to a server or programs on the server can make it easier for hackers to get in. There are hacking tools that specifically scan websites and servers for default URLs and folders, so changing default login locations is important. On this same basis, it’s a good idea to make sure that directories are protected so that people cannot see their contents.
Active Monitoring
A critical requirement to properly managing a server is knowing what is happening with it at all times. Even the best security software cannot prevent all intrusions, and hackers are constantly figuring out new ways to exploit and circumvent security systems. Therefore, it’s important that activity on a server is always being monitored. Things that normally indicate a problem include incredibly high data transfer or processing power use as well as multiple failed login attempts. Brute force hacking involves trying to login to a system over and over again with different login and password combinations. In addition to draining system resources, it can also eventually allow a hacker to find a combination that lets them into your system. Real-time monitoring can help detect these issues and alert the appropriate people, and it can also shut down brute force login attempts.
Passwords & Permissions
Another important server security measure is to ensure that all passwords, especially the root and/or Admin passwords, are complex and that people are only given access to areas that they need to do their job. Aside from malice, giving an intern administrative access to databases could lead to major problems through simple error. It’s also recommended to change your passwords on a regular basis, even if they are robust.
There are a number of ways to tackle the issue of making sure passwords are complex enough, including using computer generated passwords or using passphrases. Computer generated passwords normally require certain characters, length and require a combination of upper and lower case letters; passphrases are combinations of words, and they tend to be easier to remember and more secure than passwords. There should also be a set time that passwords expire, which will require users on the network to change them on a regular basis.
Along with ensuring that people are only given access to parts of a server that they need to have, it’s important that permissions are updated when people leave a job or move to a different part of the company. This can be done with proper database management and doing occasional audits to ensure that access levels are appropriate.
Updates
One way that hackers get into many servers is by going through weak points that developers did not notice when creating an application or an operating system. This is why both computers and mobile devices need regular updates. Along with offering new options, updates close off back doors and holes in the security of software. Therefore, it’s important that all software hosted on your server is kept up to date. For web hosting servers, that means content management systems (CMS) such as WordPress, and the plug-ins the CMS uses must be kept current. Many operating systems and software applications can be set up to update automatically, but if you’re not comfortable with that, it’s important that you have some way of being notified when important changes are available.
For those of you who feel there’s just not enough time in your day to employ these server security measures, or if you just prefer someone else does it for you, at TurnKey Internet we got your back. We offer Fully Managed solutions, such as our Best cPanel Dedicated Server, that include Server Hardening. We’ll take care of securing and protecting your server so you can focus on running your business. For more information, visit https://turnkeyinternet.net/managed/
Follow Us :
Share :
WordPress, Joomla, Drupal – Which CMS is best? no comments
In the world of Content Management Systems (CMS) there are 3 major contenders: WordPress, Joomla, and Drupal. If you are creating a new website, you may be asking yourself which one is best. All three have their own pros and cons, and all three are free to use, open-source software. Let’s take a brief look at each one to see which CMS is right for you.
WordPress
Created back in 2003 and currently running on more than 70 million websites, WordPress is by far the most popular CMS out there. It started out as just a simple blogging tool, but has evolved into a full, feature-rich, content management system. With it’s extremely easy to use interface, you can create a website in only a matter of minutes. Plus, with the endless amount of free themes and plugins available for WordPress, it’s easy to make your website look great. However, popularity does have it’s drawbacks. For instance, WordPress is one of the biggest targets for hackers. It is critical you keep it up-to-date to prevent attacks on your website. Regardless, with it’s intuitive design and countless number of free customizations, this easy to manage CMS demonstrates why it’s a popular choice.
Joomla
Considered the second most popular CMS out there, Joomla is also easy to use, but is a bit more complex and requires a higher skill level than WordPress. It has less free customizations when compared to WordPress, however when it comes to E-Commerce sites, Joomla excels and tends to be a favorite choice. It is also considered to have one of the strongest developer communities. Joomla is based on PHP and MySQL, giving more advanced developers the ability to create a powerful web application. With a minor amount of effort into learning Joomla’s terminology and structure, you can go on to create a fairly complex website. If you are looking for something still fairly easy, but with more flexibility than WordPress, Joomla might be the one for you.
Drupal
Drupal is ranked as the third most popular CMS in the world. It is regarded as the most complex, with the highest learning curve of the three. Drupal has a greater amount of free customizations and themes available when compared to Joomla, but less than WordPress. It is considered to be one of the most versatile and robust content management systems available today. When it comes to websites that contain a large amount of complex data with heavy visitor traffic, Drupal is an excellent choice due to the speed and strength from its advanced structure. However, all of this comes at the cost of needing more experience and expertise to truly utilize this powerful, developer friendly CMS. If you are looking for an enterprise-ready CMS that will scale with your growing business, look no further than Drupal.
Whether you are a beginner looking to start a blog, an expert developer creating a complex, versatile site, or somewhere in between, one of these three CMS applications will definitely get the job done. Best of all, they are free to use and support simple one-click installations. So if you are currently hosted on TurnKey Internet’s shared cloud platform or have a cPanel dedicated server, getting started couldn’t be any easier! The question then becomes not which one is best, but instead, which one is best for you.
Follow Us :
Share :
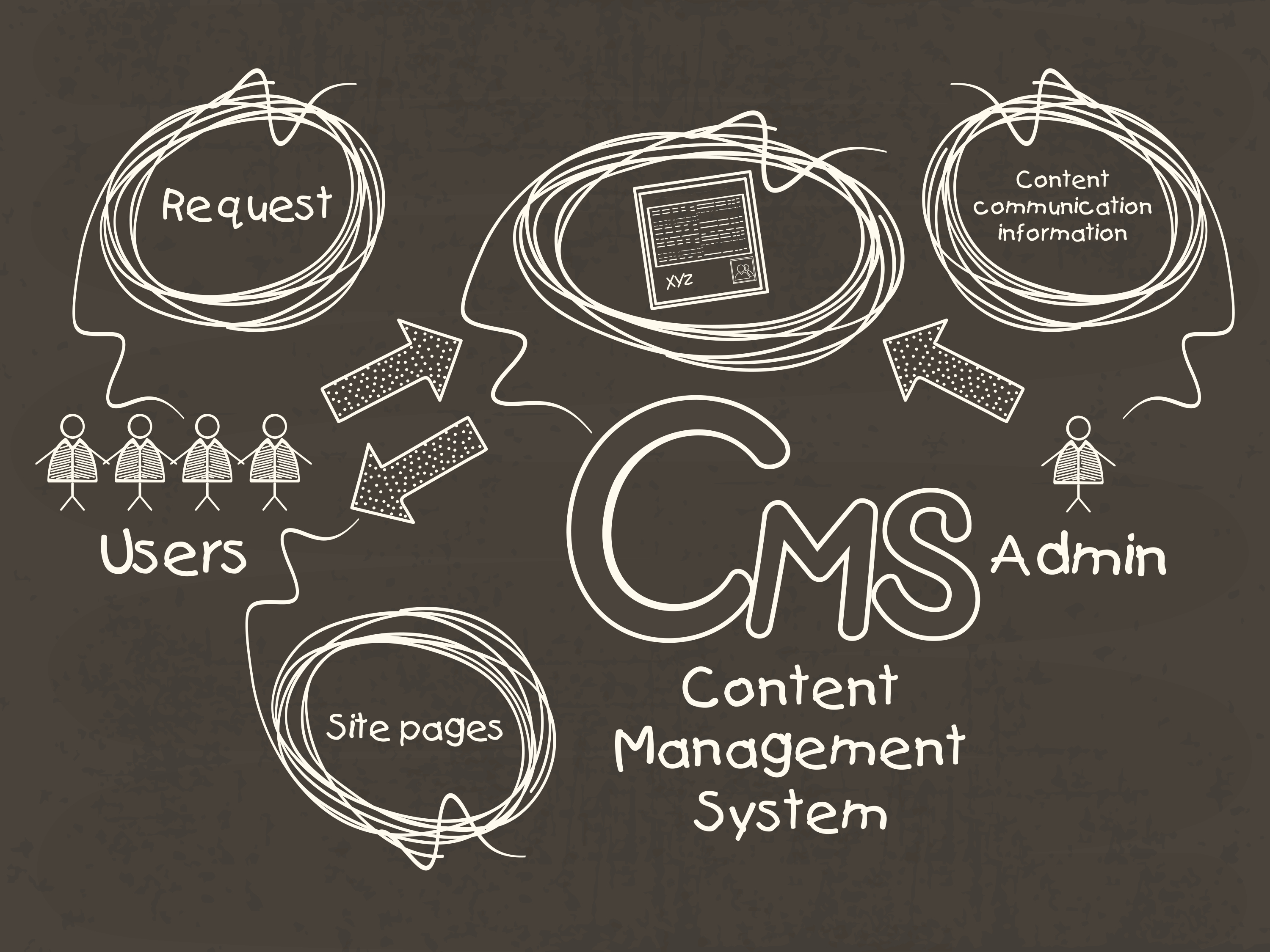
Content Management System (CMS) 2 comments
Whether you are a beginner looking to start your first website, or a tech-savvy business owner creating your company’s e-commerce store, one of the first decisions you will make is what Content Management System, or CMS, to use. A CMS is an application that supports the creation and publication of digital content and media. More importantly, a CMS allows creators with little knowledge of programming languages to easily create and manage websites and their content.
While there are various options when it comes to choosing a CMS, a few standout due to their popularity:
Drupal
Currently ranked the 3rd most popular CMS in the world, Drupal is considered as one of the most versatile, and robust systems available today. If you’re building a website that will contain a large amount of complex data, and expect to have heavy visitor traffic, Drupal is an excellent choice due to the speed and strength from its advanced structure. It also features a large amount of free themes and available add-ons. However, all of this comes at the cost of needing more experience and expertise to truly utilize this powerful, yet at times complex CMS. Drupal is enterprise-ready and will scale with your growing business.
Joomla
Next we have the 2nd most popular CMS, Joomla. When it comes to E-Commerce sites, Joomla tends to be a favorite choice for many. It’s based on PHP and MySQL, allowing more advanced developers to create powerful web applications. This has helped Joomla to build what’s considered to be one of the strongest developer communities around. With a minor amount of effort into learning Joomla’s terminology and structure, you can go on to create a fairly advanced website.
WordPress
Finally, we have by far the most popular CMS out there, WordPress. Back in 2003, WordPress started out as just a simple blogging tool. Today, it has grown into a full, feature-rich, content management system, that is currently running on more than 75 million websites. With it’s extremely easy to use interface, you can create a website in only a matter of minutes. Plus, with the endless amount of free themes and plugins available for WordPress, it’s easy to make your website look great. However, popularity does have it’s drawbacks. For instance, WordPress is one of the biggest targets for hackers. It is critical you keep it up-to-date to prevent attacks on your website. Regardless, with it’s intuitive design and countless number of free customizations, this easy to manage CMS demonstrates why it’s a popular choice.
All three CMS applications listed above have their own pros and cons, but a benefit they all share is that they are free to use, open-source software. Plus to make things even easier, they all support simple one-click installations. Need help getting started? At TurnKey Internet, our Cloud Solution Specialists are here to assist. Contact us today!
Follow Us :
Share :
Securing WordPress against the Hordes of Bots no comments
WordPress is one of the most popular, third party scripts used on websites. Each and every time WordPress releases an update or a patch, the reasoning behind the update is publicly released but often its security related. This is for all developers to be aware and update their code accordingly. This factor alone, makes your site targeted. Not to scare anyone reading this, however in a recent study WP White Security reported 70% of WordPress sites are vulnerable to attacks!
The majority of hacked sites are compromised for the sole purpose of sending spam. TurnKey Internet and other web hosting services cannot guarantee your site will not become compromised due mainly to third party scripted plugins and modules that often modify or alter WordPress in ways that even the main security aspects of WordPress can’t anticipate. TurnKey Internet makes sure your site is secured against a large scale of attacks and has a restoration plan if needed utilizing our multiple online cloud backup services we offer with our hosting services . The last thing a hacker wants to do is spend a large amount of time accessing your site. The more road blocks, the faster the malicious user will lose interest and move on.
Before I get too far ahead of myself, let me first explain how your site becomes compromised. I believe this is important when securing your site. Understanding how malicious users are gaining access and what the user is doing. While there is a vast scale of techniques a hacker can use, the main way a malicious user will gain entry to your WordPress site was grouped in the following categories by WP White Security:
41% – Security vulnerability on the hosting platform. Nothing to worry about on TurnKey Internet’s web hosting server platforms, as we are constantly updating the servers with the latest security releases and patches. As well as keeping all services on the server up to date in addition to having the most advanced firewalls and intrusion detection systems in place. If you have a dedicated or VPS server and would like to TurnKey to review your server, shoot us a support ticket we’d be more than happy to investigate.
29% – Outdated WordPress Theme which can open security holes
22% – Outdated WordPress Plugins which can open security holes
51% of reported compromised sites are due to an outdated theme or plugin. This is completely preventable! When your plugin or theme is compromised, this makes it possible for a hacker to inject an eval base 64 decode code. This allows the hacker to run a PHP function from the site. These are PHP mailers the malicious user users to send spam from your account.
8% – Due to a weak password. This is where brute force attacks are successful. Hackers use a script to continuously generating random passwords, until they have gained access to your dashboard.
First and foremost, make sure everything is updated to the latest version. Each time WordPress releases an update, the update is addressing a security threat. This is why keeping the script updated is important. As mentioned previously, due to the popularity of WordPress the exploits patched are publicly released. This allows developers to adjust their coding accordingly.
In version 3.7, WordPress added in the feature to allow automatic updates. This sounds wonderful, except by default it only applies to minor updates. The WordPress team did this to prevent sites from automatically breaking when updated. (Typically this happens if your plugins are not continually updated by the developer.) You can add the following lines of code to the wp-config.php file and all updates will be automatic.
# Enable all core updates, including minor and major:
define( ‘WP_AUTO_UPDATE_CORE’, true );
Alternatively, if you would like to take control and complete all the updates yourself, you can add these lines instead.
# Disable all core updates:
define( ‘WP_AUTO_UPDATE_CORE’, false );
Since more than half of WordPress sites are hacked due to outdated themes or plugins, be picky as can be with the ones you activate. Pay attention and investigate the themes and plugins you are using.
Not all plugins and themes are actively maintained by their developers. Only use plugins that are updated regularly. If the plugin or theme hasn’t been updated in 6-9 months, there is a good chance the developer is no longer maintaining their theme or plugin. Stick with WordPress developers. You can download tons of plugins and themes directly from WordPress.org.
Do you honestly need that plugin? If it is not necessary for your site, deactivate it and remove it. Not only does it take your site longer to load, you’re providing more chances for a malicious user to find a backdoor.
Lock down who has access to your WordPress dashboard. The easiest way to complete this is by adding a few lines of code into your .htaccess file. As with all aspects of web hosting case sensitivity is important. Please note where the capitalization is when implementing this code into your .htaccess file.
<Files wp-login.php>
order deny,allow
Deny from all
Allow from 111.111.111.111
</Files>
You will want to exchange 111.111.111.111 with the IP address of the machine you are connecting from. If you are unsure of the IP, Google “what is my IP” from the device you would like the IP of.
Hey, that’s great but what if I need to access the dashboard from the office and from home? No worries, you can add additional ‘Allow from’ statements.
<Files wp-login.php>
order deny,allow
Deny from all
Allow from 111.111.111.111
Allow from 222.222.222.222
</Files>
Limit the number of login attempts an IP address can have before your server blocks the IP. If this is a new install, using Softacoulous, there is an option ‘enable the number of login attempts’ listed in the preinstall screen. If you have already installed WordPress, I recommend using the Limit Login Attempts plugin.
Do not use the default “admin” username. On new installs you are given the ability to make the username. If you already have WordPress installed you can change the username in the dashboard. Once logged in, access account setting, and click the “change” link next to your username. From there you can follow along with WordPress to change the username.
Change your passwords often and make sure you are using a strong password. I know this can sometimes be overwhelming and often hard for some uses to remember. However, it is extremely important to use. A good way to remember the password is to use a short sentence or phrase. Make sure to do something like replace vowels with number or make them capital.
W3bh05t1ngK1ng
1R0ckth3w3B
The above are far more secure than using:
password
123456
Johnny
Change the WordPress default table prefix. If you’ve noticed all your core WordPress files start with ‘wp’. wp-config, wp-login, wp-admin, ect. Changing the prefix can help prevent against SQL injections.
The table prefix is defined in the wp-config file.
$table_prefix = ‘wp_’;
PLEASE NOTE – Changing the table prefix in the wp-config file will not change the tables in the database.
In a fresh install you have the ability to set the table prefix to something other than wp. If you have already installed WordPress, I have found the iThemes Security plugin to be the quickest way to compete this task. If you prefer to not have a plugin complete this task, you can do so manually. It is a bit time consuming and you will need to make sure to rename each WordPress table, update the usermeta table and update the options table. Of course you will want to backup the database, before making any changes.
Make sure your file permissions are correct. WordPress states only the following permissions should be used;
Directories should be 755 or 750
Files should be 644 or 640
Your wp-config.php should be set to 600
Your wp-config file is extremely important. I recommend protecting this file in the .htaccess as well. To do so place the following lines of code inside your .htaccess file:
<files wp-config.php>
order allow,deny
deny from all
</files>
Speaking of protecting important files. The wp-includes directory contains the majority of files needed to run WordPress. There is absolutely nothing in this directory a user will need. With that being said, I recommend adding the following lines of code to the .htaccess file to protect these files as well.
# Block the include-only files
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+.php – [F,L]
RewriteRule ^wp-includes/theme-compat/ – [F,L]
</IfModule>
Block out access to the xmlrcp.php file as well.
<Files xmlrcp.php>
order allow,deny
deny from all
</Files>
xmlrcp.php, this file is the worst! While the features of using this file sound neat. (Connect to your blog via text or email, sends tracebacks or pings.) This file has been used to take down a large number of server by implementing DDOS attacks with this file. You can read more on these attacks here – https://blog.sucuri.net/2014/07/new-brute-force-attacks-exploiting-xmlrpc-in-wordpress.html
Since we are already protecting our files in .htaccess, might want to protect .htaccess as well. To do use this code.
<Files .htaccess>
order allow,deny
deny from all
</Files>
Great, now my site is secured. What about that restoration plan you mentioned earlier?
Backup, backup, backup! I cannot stress this enough! If by chance a hacker is able to break through all these security measures we have put in place, the fastest way to get your site backup is by restoring a backup.
Depending on what service you have with TurnKey, we do provide backups. However, it is not the responsibility of TurnKey to maintain your backups. You should not rely on our backups and keep your own backups as well. Our terms of service allows for you to keep one (1) full account backup stored on the server. TurnKey recommends taking backups of your account weekly or even daily. Connecting with an FTP client and storing the backup in a secure location.
While WordPress does off automatic updating services, we have disabled some of the PHP features required for this service to work on our shared hosting platforms. The reasoning on this, we do not allow for the use of PHP execute. This is for security purposes.
Inside your control panel you have the ability to take full account backups and database backups. I strongly recommend doing so.
TurnKey also offers a backup add on service called TurnKey Vault which we highly recommend for anyone with a dedicated or cloud-based server, so you can protect your data If you need any assistance with competing any of the tasks listed in this blog, email our support team (helpdesk@turnkeyinternet.net) and we would be happy to assist you.
Happy blogging!
Follow Us :Share :
Drupal Web Site Security Alert : Forged Password Reset URLs no comments
 While you may have been urged by Drupal to update your software late in 2014 due to SQL injection attacks in compromised Drupal 7 sites. Drupal has released version 6.35 and 7.35 to address a few newly discovered vulnerabilities within their software.
While you may have been urged by Drupal to update your software late in 2014 due to SQL injection attacks in compromised Drupal 7 sites. Drupal has released version 6.35 and 7.35 to address a few newly discovered vulnerabilities within their software.
Listed in an advisory by Drupal’s security team, Drupal stated one of the vulnerabilities they are addressing has allowed password reset URLs to be forged. This allows malicious users to gain access without knowing the password.
In Drupal 7 this vulnerability is segragated to sites where accounts have been imported or edited in ways that will result in the password hash, in the database being the same for multiple user accounts.
In Drupal 6 this vunlnerability can be exploited on sites where administrators have created multiple user accounts with the same password. As well as where accounts have been imported or edited in ways that will result in the password hash, in the database being empty for at least one user account. Drupal 6 sites having an empty password hash, or a password with an easily compromised string in the database are extreamly prone to this vulnerability.
The second vulnerability Drupal’s team has patched is the ability for malicous users to devise a URL, sending visitors to a 3rd party website.
Drupal modules use a destination query to redirect users to a new destination after completing an action. Malicious users can use this destination parameter to construct a URL that will fool users by redirected them to a 3rd party website. Several URL related API functions in Drupal 6 and 7 can be fooled into passing through external URLs when that was not the intention, leading to open redirect vulnerabilities.
This vulnerability is has been down played as a large amount of the destination parameter are not vulnerable to the attack. Although, all confirmation forms built using Drupal 7’s form API are vulnerable! Drupal has also stated some Drupal 6 confirmation forms are vulnerable too.
Drupal versions affected:
Drupal core 6.x versions prior to 6.35
Drupal core 7.x versions prior to 7.35
How to rectify these vulnerabilities? Update to the latest versions.
If you use the Drupal 6.x upgrade to Drupal core 6.35
If you use the Drupal 7.x upgrade to Drupal core 7.35
For those using TurnKey Internet’s Web Hosting with Drupal can simply login to your cPanel control panel, click on the Softaculous icon, and update your drupal version from there as well as from the Drupal Control panel of your installated copy on your web site. If any questions contact our customer service team, or keep posted on our help desk at http://helpdesk.turnkeyinternet.net/
Follow Us :Share :
Search Engine Ranking Benefits through SEO and IP Addresses – Google Says So! no comments
 Did you know in August 2014, Google announced that HTTPS would become a ranking credential? This is news worthy of mention and note as Google rarely reveals ranking criteria – and more so confirms that the SEO optimized hosting at TurnKey in fact does raise your rankings for SEO systems (at least with google, now confirmed).
Did you know in August 2014, Google announced that HTTPS would become a ranking credential? This is news worthy of mention and note as Google rarely reveals ranking criteria – and more so confirms that the SEO optimized hosting at TurnKey in fact does raise your rankings for SEO systems (at least with google, now confirmed).
You can read more about Google’s comments here: HTTPS as a ranking signal here. [PDF ]
HTTPS is an added layer of encryption that Secure Socket Layers on top of HTTP or web traffic. This adds additional security to standard HTTP communications or web communications. SSL certificates are required for
e-commerce sites especially if you’re desiring your site to be PCI compliant. You can see my post on PCI compliance here: https://blog.turnkeyinternet.net/web_hosting/pci-dss-compliance-in-the-cloud-for-web-sites-servers-and-colocation/ . Having an SSL certificate is essential on an ecommerce site because of the secure transmission of sensitive information like credit card numbers, personal information, and login accounts.
If your website or blog begins with https://, you have likely received an uptick in Google’s rankings. This is currently a lightweight signal meaning that it doesn’t affect your site rankings greatly, but experts believe it will become stronger in the near future.
To turbo charge your web site’s rankings, be sure to use SSL certificates with a dedicated ip address on your web site, TurnKey offers an all-in one ‘turnkey’ solution to this to help you increase your search engine ranking with our Turbo SEO cPanel Web Hosting that bundles in multiple dedicated class-c ip’s and ssl certificates for one low cost in a simple to use interface.
Do You Need an SSL Certificate for Your Website?
REQUIRED: All websites should have some form of protection on them. This form of protection can come in many forms, however, if you’re going to be taking any type of data from your customers such as credit cards, phone
numbers, emails, or any personal information, you need to ensure that the data is transferred securely. SSL’s remain one of the most robust ways to do this.
As an online merchant, it’s your responsibility to make your customers’ private information is secure. If you are storing credit card information in a database on your website so you can manually charge it later, then you need an SSL certificate to secure the credit card data stored on your server. If you have any sort of log-in form where customers enter a username and password, on top of sanitizing the input from the user, a SSL certificate is highly recommended.
NOT REQUIRED: An SSL certificate is optional if you don’t gather personal information and instead forward your customers to a 3rd party payment processor like PayPal. This can be done as simply as embedding a PayPal button to your website. PayPal uses their own certificate to encrypt customers transactions. HOWEVER, you can still benefit with SSL for search engine rankings, so it’s worth the investment but not REQUIRED for this category.
What Webmasters Should Do Now?
Decide the kind of certificate you need: single, multi-domain, or wildcard certificate. (More on this in a minute.)
Use 2048-bit key certificates. Use relative URLs for resources that reside on the same secure domain. Use protocol relative URLs for all other domains. Don’t block your HTTPS site from crawling using robots.txt. Allow indexing of your pages by search engines where possible by avoid the noindex robots meta tag.
Purchase an SSL Certificate from TurnkeySSL.com
Turnkey Internet is a trusted reseller of GlobalSign SSLs. The GlobalSign SSL certificates includes domain validation, quick issuance, re-issues among many other options such as adding a full trusted bar in your browser that allows visitors to see your SSL is trusted across the web.
Turnkey Internet has multiple types of SSL certificates for secure communication with business, system, portals, mail and more.
Our TurnKeySSL alpha certificate is ideal for small business, blogs, and personal websites which costs $29 per year.
The TurnkeySSL Professional certificate is ideal if you wish to have multiple subdomains covered (example: corp.yourdomain.com and web.yourdomain.com). This Pro level SSL certificate has full organization vetting which provides higher levels of trust and includes a malware site scan service. This is also preferred for service providers and SEO companies. $150 per year.
Lastly, TurnKeySSL Extended Validation (EV) Certificates are the most secure and offer visitors the green bar and enhanced sales. It also includes malware site scan service. The green address bar that comes with a TurnkeySSL Extended certificate prominently displays your company name, providing immediate trust and improving customer conversions. This certificate is $899 per year.
Keeping your certificate always up to date is recommended as you never want your clients receiving any SSL warnings when purchasing a product from you. Ideally,you would set the certificate to auto-renew annually. You can always check the expiration date by clicking the padlock symbol and then “View Certificate”. Test your entire checkout process in Firefox, Google Chrome, and yes, even Internet Explorer.
Once again, you can go directly to turnkeyssl.com to purchase any of the mentioned SSL types above
To turbo charge your web site’s rankings, be sure to use SSL certificates with a dedicated ip address on your web site, TurnKey offers an all-in one ‘turnkey’ solution to this to help you increase your search engine ranking with our Turbo SEO cPanel Web Hosting that bundles in multiple dedicated class-c ip’s and ssl certificates for one low cost in a simple to use interface. Learn more
Until next time…
Share :
Locked out of cPanel Again? Locked out of your Web Site? no comments
 Avid readers of the blog know that I’m a slayer of tickets and protector of the Turnkey Internet realm of support tickets. If you have a support need with your software that you’ve purchased from Turnkey Internet, more than likely, I will be one of the team members who works on your issue. I wanted to write you gentleman and ladies, a post on a support request I see at least once a week if not more. I will start this article off by asking one question. Have you ever been locked out of your house? You walk out the house not thinking about the door, but then you realize that you need to go back into the house to grab your keys. However, the door is locked.
Avid readers of the blog know that I’m a slayer of tickets and protector of the Turnkey Internet realm of support tickets. If you have a support need with your software that you’ve purchased from Turnkey Internet, more than likely, I will be one of the team members who works on your issue. I wanted to write you gentleman and ladies, a post on a support request I see at least once a week if not more. I will start this article off by asking one question. Have you ever been locked out of your house? You walk out the house not thinking about the door, but then you realize that you need to go back into the house to grab your keys. However, the door is locked.
What will you do? If you’re a super prepared individual, you may have a spare key laying around somewhere, but if you’re like me, this may not be the case. So, what’s next? Maybe you start thinking, “hmmmm, I wonder if I have any windows unlocked?” You walk around the house hoping, praying, that you have a window unlocked. You soon discover, that you’re a very safety conscious individual and all of your windows are locked? Well, what do you do now? You have no spare key. No windows are unlocked. While that rock on the ground could easily go through the window, do you really want to pay money to get the window repaired?
This usually leaves you with no other option then contacting your local locksmith. Pay the ridiculous amount to have them drive out and let you back into your house in a matter of minutes. Now, what if that happens on your server? For the sake of this article, we will assume you have a server, VPS/Dedicated/Cloud, that has cPanel installed. You haven’t changed the password, but all of a sudden you can’t login to your cPanel or WHM anymore. What do you do? Well, if you purchased your services from Turnkey Internet, the quickest way would be to open a support ticket and have one our engineers allow you back in, but what if you’re a do it yourself type of person? Is there a back spare key you can use?
Now, just to be clear, I’m not talking about not being able to view your site in a browser, but specifically about your cPanel password, that you’ve not changed, no longer working. You may get the first thought that, holy crap, my account has been hacked. Someone has stolen my password and is slowly but surely stealing all of my data. While yes, this could be a possibility especially if you have an insecure password, e.g. CAT123, but what if you have a secure password. A 12 character password. It’s more less likely that your cPanel password has been stolen and more likely that you’re locked on our your account by cPHulk.
It’s very possible that you’ve heard of cPhulk before. For those of you who haven’t, the link below will explain exactly what cPHulk is:
http://docs.cpanel.net/twiki/bin/view/11_30/WHMDocs/CPHulk
cPhulk is a brute force protection software that is installed by cPanel by default. This little piece of software constantly monitors the server to ensure no one is brute forcing their way into your server. For users who do not know what brute forcing is, please see the link below:
http://en.wikipedia.org/wiki/Brute-force_attack
To summarize that link, brute forcing is when a hacker tries every iteration possible to login to your account. They start with a dictionary of commonly used username and passwords and attempts to login to your account with each one. This is called a brute force attack and is what cPHulk is written to protect against. However, cPHulk can be a bit over zealous at times and end up blocking you out of your own accounts. So, how do you fix?
This fix assumes that you have root access to the server and a SSH client such as Putty to access the server.
- SSH to your server
- Type mysql
- Connect cphulkd;
- Delete from brutes;
- Delete from logins;
That will clear all IP’s currently blocked on the server and allow you to login to cPanel/WHM. At which point, you can go to Security Center -> cPHulk Brute Force Protection and white list your own IP to keep this from occurring in the future. You’ve essentially just become your own cPanel locksmith. If you’re still having issues, you can always open a support ticket with us directly at: https://helpdesk.turnkeyinternet.net/
Until next time…
Follow Us :Share :
Is your wordpress web site under attack? Over 90,000 hacker bots may be knocking on your door! no comments
I have a quick question for you, have you ever heard of wordpress? My guess is since you’re reading this blog, you’ve heard of wordpress any may even be using on your own website, but for those who are first time readers, I will give a brief overview. Here is a quick overview from WordPress.org:
WordPress is web software you can use to create a beautiful website or blog. We like to say that WordPress is both free and priceless at the same time. The core software is built by hundreds of community volunteers, and when you’re ready for more there are thousands of plugins and themes available to transform your site into almost anything you can imagine. Over 60 million people have chosen WordPress to power the place on the web they call “home” — we’d love you to join the family.
WordPress is one of the most popular site building pieces of software currently on the internet. Sure, you have Joomla which is almost the same as wordpress, but has slight differences with its configuration. For this article, however, we will be focusing purely on wordpress. As you can see in the overview above, over 60 million people have chosen to use wordpress which is quite a large pool of users on the internet. Now, what if someone decided to launch an attack on wordpress based sites? They would have a pretty large base of users to attack and could affect hundreds or possibly, thousands of websites. Well, this attack has already happened and still running at this very instance.
On an off for the last few months, A botnet of over 90,000 machines, has been attempting to globally brute force and hack into wp-login.php which is the file that WordPress users use to login to WordPress. The attack is sending thousands of requests at one time to attempt to login to your WordPress installation via wp-login.php in an attempt to gain access to make it part of the growing botnet. To shed some light on what a bonet is, directly from Wikipedia:
A botnet is a collection of Internet-connected programs communicating with other similar programs in order to perform tasks. This can be as mundane as keeping control of an Internet Relay Chat (IRC) channel, or it could be used to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation.
Well, you may be wondering, if I have a site on a server with Turnkey Internet, how are my sites being protected? Since day 1 of the wide scale attacks, we’ve enabled a server wide ACL that blocks all access to wp-login.php unless the IP is whitelisted. This ACL or access control list, keeps the attack at bay. Due to the fact that the botnet is targeting wp-login.php directly, we can deney all access to users we specifically allow. When the attack runs, our servers return a 403 page and the attack moves on. You may be saying, “Sure, that works, but is there anything that I can do as a client on my end to help relieve the attack?’
Listed below is the recommended code that you add to your sites .htaccess file in your public_html folder to add an extra layer of security (you’ll need to edit ‘example.com’ to be the domain you are setting it up on):
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{REQUEST_URI} .(wp-comments-post|wp-login)\.php*
RewriteCond %{HTTP_REFERER} !.*example.com.* [OR]
RewriteCond %{HTTP_USER_AGENT} ^$
RewriteRule (.*) http://%{REMOTE_ADDR}/$ [R=301,L]
</ifModule>
This in conjunction with our ACL will prevent the attack from affecting your site(s).
Additional recommendations:
-Changing your default admin username for wp-admin to a different username as the attack is specifically targeting the admin username.
-Placing a browser-based password on wp-login.php
The link immediately below will explain how to do this:
http://codex.wordpress.org/Brute_Force_Attacks#Password_Protect_wp-login.php
Additional information about the attack can be found here:
http://blog.skunkworks.ca/brute-force-attack-targeting-sites-running-wordpress/
http://www.inmotionhosting.com/support/news/general/wp-login-brute-force-attack
Using the tips we’ve provided above, this will help to keep the attack from affecting your site. It will also increase the security of your wordpress based site as well. We hope this will help all clients and not just those at Turnkey Internet, but any client globally who may be having issues with the wordpress attack on their sites.
Until next time
Share :
Big news from the Tech Cave – World-wide attack on WordPress! no comments
 As you know, we’re big on making sure that you’re all happy as clams with the service you’re receiving from us. How happy is a clam, you ask? I don’t know. I don’t even know where that expression came from, and that’s not important right now.
As you know, we’re big on making sure that you’re all happy as clams with the service you’re receiving from us. How happy is a clam, you ask? I don’t know. I don’t even know where that expression came from, and that’s not important right now.
Anyway, I feel it is important to give you blog readers a heads up on a crazy, world-wide WordPress attack that might be affecting your service, just in case you haven’t stopped by the TurnKey Helpdesk recently. I just had a chat with our Operations Manager, Brian, and since he basically sleeps in our cold containment pods, what you’re about to read is fresh from the kitchen. Watch your hands—the plate is hot…
There is currently a world-wide attack affecting all WordPress sites at all hosts. This is an attack of unprecedented nature, from a botnet operating on 90,000+ IP addresses.
Due to the nature of the attack, memory consumption on targeted servers has increased. In some cases, this has resulted in degradation of performance and unresponsive servers. This is due to a high volume of ‘http’ requests, which can cause some servers to start swapping memory to disk, and possibly run out of memory. We’ve put measures in place at the firewall and at server level to off-load a lot of the attack, however, there isn’t much more we can do at this time. We have disabled all access to wp-login.php to ensure none of our customers are at risk. For those customers needing to log into their WordPress sites, please open a ticket with our support team, and we can provide access to your sites.
We are working closely with our security and channel partners to further address the issue as it becomes possible.
Again, we feel it’s important to stress that this is not a TurnKey-specific issue. Brian and I took a peek around, and it seems like everyone, everywhere is fighting the same, annoying battle.
We’re super grateful for your understanding and patience while the attack runs its course. If you would like further assistance, or have any additional questions, feel free to contact us by phone or email, Live Chat, Facebook or Twitter—however you would like. Owl? Sea plane? Regardless, we’ll be listening. Sit tight, and we will iron this out as soon as possible.
Follow Us :Share :